ThreatFabric analysts have discovered a new banking malware dubbed BlackRock capable of stealing card details and passwords.
According to researchers, BlackRock is an extremely dangerous malware that can silently empty your bank account. The malware derived from the code of a banking virus family born in 2016 — LokiBot, which later became MysteryBot (2018), then Parasite (2018), then Xerxes (2019) and, now, on May 2020 spotted as BlackRock.
The functioning of the latter malware is similar to that of its predecessor but undergo changes in its code. Additionally, BlackRock malware allegedly leaves no trace of the stealing of data or hacks. One functionality that is so far unique to BlackRock is that it makes usage of the Android work profiles — which allows controlling various aspects of a device without per se having complete administration rights on all aspects of the device.
Researchers also discovered that BlackRock’s target list includes 337 android apps — means this banking trojan not only targets financial apps but also steals credentials of important social, networking, communication, and dating applications too.
Some of the popular apps targeted by the BlackRock malware includes PayPal Mobile Cash, Gmail, Yahoo Mail, Microsoft Outlook, Amazon seller, Skrill, Uber, Netflix, Amazon shopping, Binance, YONO Lite SBI, IDBI Bank Go Mobile+, and iMobile by ICICI. The complete list of infected apps already discovered by ThreatFabric has been published in the report.
How BlackRock works?
BlackRock functions like any other trojan — As soon as it enters the Android smartphone, it hides its icon from the app drawer to make itself invisible to the user. The malware enters the device pretending to be a Google Update at first, and then it asks the victim for the Accessibility Service privileges.
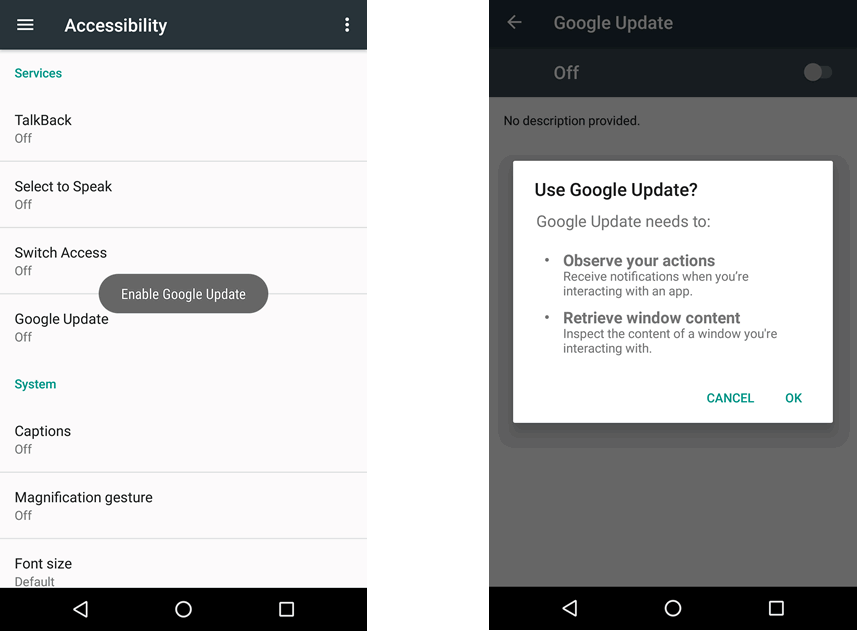
And once the user grants the requested Accessibility Service privilege, BlackRock starts working by granting itself additional permissions until the device is practically under complete control.
How dangerous is BlackRock?
When BlackRock took control of the smartphone, it can do many dangerous things. First, it tries to spread further by accessing the contact list and starts to send messages to everyone, even every 5 seconds, and then set itself as default SMS manager. Also, it can deactivate apps, including any Android antivirus, and finally, it can also take possession of the management of notifications.
But the most dangerous of all is — BlackRock can do the “Keylogging” that is, it can spy and record the keys that we press on the smartphone. And this is the primary method used by this malware to steal the data of users’ online accounts and credit cards registered on the device. In a short time, therefore, this virus can access our financial apps and get hands-on users’ money.
Malware attacks on Android have been kept increasing. Recently Google has removed 11 apps infected with joker malware from Playstore. And now ThreatFabric reports show at present 337 apps are vulnerable to BlackRock banking trojan.
