At the Virus Bulletin 2020 conference, the Facebook security team revealed one of the most challenging malware operations it has ever faced.
Malware attack known internally at Facebook as SilentFade, has been going on for at least two years since it was in 2018 when the company first became aware of strange behavior in some accounts, without the users themselves noticing.
Specifically, some employees noticed that someone was changing the settings related to notifications — turning them all off. So that victims wouldn’t realize that someone is using their account by not receiving notifications of messages or mentions, for example.
Facebook has revealed the details of the internal investigation that its investigators have carried out to find the cause and the objective of these attacks.
The main target of these hackers, as you might guess, were Facebook users. The attackers used Windows Trojans, browser injection, scripting, and even vulnerabilities in the Facebook platform for their campaigns. The hackers “task was to infect users with a Trojan, take control of their browsers, and steal passwords and cookies to gain access to the victims” social network accounts.
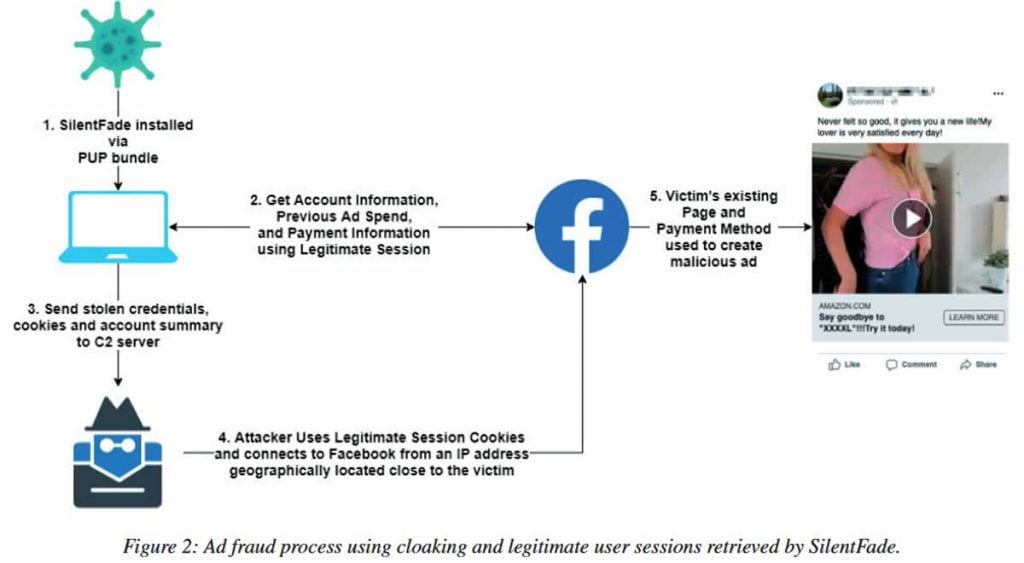
First of all, the hackers were interested in the accounts that had any type of payment method attached to their profile. On behalf of such accounts, SilentFade bought ads on Facebook, of course, using victim’s money.
Although the group’s activity lasted only a few months, according to Facebook, during this time, the fraudsters managed to deprive users of more than $4 million — all of which was used to place malicious ads.
Facebook security took notice of SilentFade in February 2019 when users began to complain of suspicious activity and illegal transactions originating from their accounts.
Since then, the company has focused not only on plugging the flaw that does SilentFade work but also on finding those responsible. For the latter, Facebook filed a lawsuit last December against a Hong Kong company and two Chinese citizens for their participation in the creation of this malicious program.
However, that does not mean that the story is over. Facebook itself warns that the danger is not over and that maybe, in the coming days, similar attacks will become very popular among hackers on all social platforms.
In fact, Facebook claims to have discovered SilentFade-like tools for other services such as Twitter, Amazon, and Instagram during the investigation. That is why the tech giant has taken advantage of the research publication to ask for more collaboration between the large social networks and antivirus developers.
Facebook proposes that more information be shared, as companies are typically able to see such unusual behaviors on their platforms, and antivirus vendors can see spikes of infected systems simultaneously. Sharing those discoveries could fix problems faster.
