After the forensics software manufacturer Cellebrite falsely announced last year that it had figured out a way to access the secure messaging app Signal. It looks like now Signal has turned the tables.
With a blog post, Signal creator Moxie Marlinspike claimed that his team was able to hack the Cellebrite forensics tool and discovered several critical vulnerabilities. These security gaps are so serious that the forensic results of current, as well as past and future investigations, can be manipulated.
Cellebrite’s software is aimed at governments and police forces, including authoritarian regimes, who use the software to track journalists and activists. These can forensically read and process smartphones with the programs UFED and Physical Analyzer. The prerequisite for this is that the authorities have physical access to a smartphone — when it is unlocked.
“When Cellebrite announced that they added Signal support to their software, all it really meant was that they had added support to Physical Analyzer for the file formats used by Signal.” — writes in his blog. And thus laconically comments on what the alleged signal hack was all about.
“This enables Physical Analyzer to display the Signal data that was extracted from an unlocked device in the Cellebrite user’s physical possession.” Under these conditions, an intruder could simply open the Signal app — or any other app — and read the messages there and take screenshots if necessary.
The software from Cellebrite processes the data, however, so it is easier to analyze it. In order for this to work, the physical analyzer has to process a large number of different formats from an untrustworthy source — for example, a confiscated smartphone.
To be able to display media data, Cellebrite also uses the open-source library FFmpeg. However, in a version from 2012 that Cellebrite has not updated since then. “During this time, there were over a hundred security updates, none of which were installed,” writes Marlinspike.
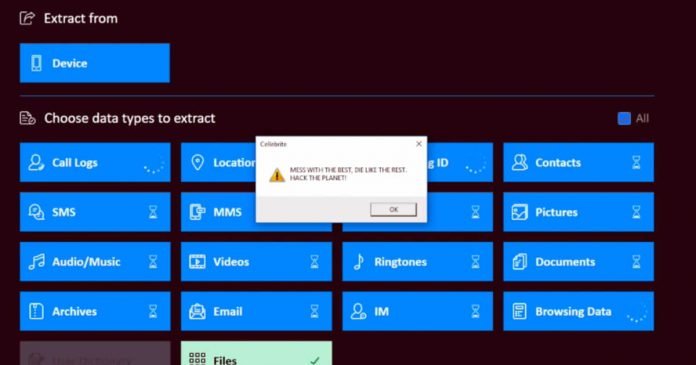
With specially prepared files that the software reads from a smartphone, the security gaps can be exploited, and any code can be executed on the Cellebrite computer. There are practically no limits to the code that can be executed, explains Marlinspike. The procedure is demonstrated in a proof-of-concept video.
This means that not only the current forensic analysis of a smartphone can be manipulated, but also the Cellebrite reports of all devices scanned before or in the future, according to the blog entry.
This seriously questions the credibility of the reports from Cellebrite, since every app could contain such a prepared file, writes Marlinspike. The use of such reports as evidence in court is therefore questionable.
In addition, Marlinspike announced that the upcoming version of Signal would regularly retrieve such files and store them in the app memory. “These files are never used for anything inside Signal and never interact with Signal software or data, but they look nice, and aesthetics are important in software,” Marlinspike writes wittily.
“We are, of course, willing to responsibly disclose the specific vulnerabilities we know about to Cellebrite,” writes Marlinspike. However, this will only be done on the condition that Cellebrite reports all vulnerabilities to the respective manufacturers that they use for their software and services — now and in the future.