The Zimperium zLabs security team has discovered a new dangerous Android malware, named GriftHorse, that has already affected 10 million devices in 70 countries around the world.
GriftHorse, a Trojan found in applications that appeared to be legitimate but silently subscribed victims to premium SMS services. According to the security experts, it has been active since November 2020, and GriftHorse operators are believed to “earn” between $1.5 million and $4 million a month. They even qualify GriftHorse as one of the most “widespread” malware campaigns of 2021.
This research has been made public on the Zimperium blog, with the collaboration of researchers Aazim Yaswant and Nipun Gupta. They have detailed the way that malware works.
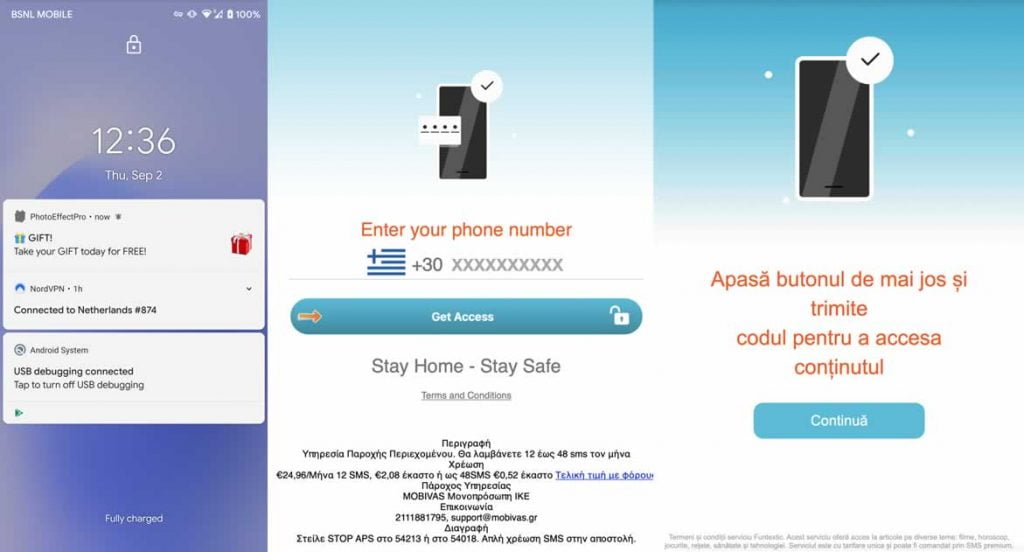
The versions of GriftHorse noticed by experts were distributed through the official Google Play store and third-party application catalogs — disguised as other harmless applications. By installing itself on the victim’s phone, it fills the device with so-called popups that show forged advertisements and, above all, false notifications of prizes, offers, etc.
If the victim clicks on one of these notifications, they are redirected to a page where they are asked to verify their phone number, ostensibly to access the offer. In fact, here, users subscribe to paid SMS services, the cost of which sometimes exceeds $35 per month. This money ends up going into the pockets of the GriftHorse operators.
The campaign uses at least 200 trojanized mobile apps, making it one of the largest fraudulent transactions uncovered this year. Malicious apps fall into a variety of categories ranging from Tools and Entertainment to Personalization, Lifestyle and Dating, allowing attackers to scale up their attacks.
Like banking Trojans, GriftHorse does not exploit any vulnerabilities in the operating system but uses social engineering techniques to force users to subscribe to a premium service.
The researchers reported their discovery to Google, and the rogue apps were removed from the Play Store. However, they are still available in untrusted third-party repositories.