The threats and attacks to which the cybersecurity of companies is exposed are increasing, their number continues to grow, and they are also becoming more complex. This situation means that the traditional tools that offer protection are not enough.
Today’s corporations need solutions with security models that are capable of offering maximum protection to their networks, terminals and data.
We have already seen that the risks to which companies are exposed when working with internet services and applications can occur at different levels. To deal with them, the most optimal thing is to configure, through good security measures that offer multiple layers of defence, so that the attack that penetrates one of them can be stopped at the next layer.
Contents
A Multi-Layered Defense To Protect Your Business
System-level security
It is the last line of defence against threats and attacks on the internet and is the first step to configure in any security strategy. A good security system must meet certain characteristics — the system must be backed by a professional company that responds to any incident, and it must have quality seals that guarantee its proper functioning.
Network-level security
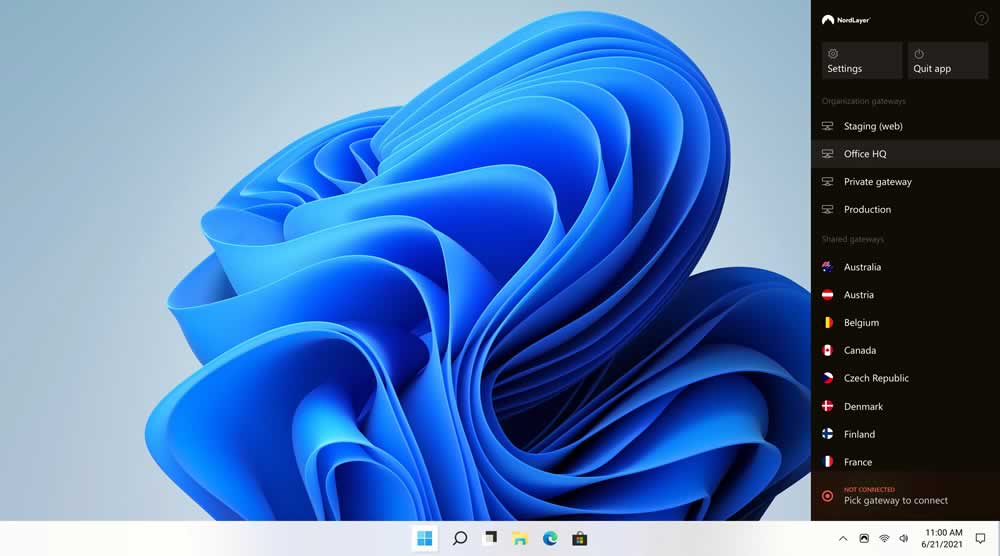
These types of measures control access to network systems. Today, a network-level security tool, like NordLayer, with a built-in firewall covers this vulnerability by using multi-layered network security features. NordLayer protects your system by setting up virtual locations for your organization and preventing unauthorized data access. It also auto-connects to a VPN server as soon as an internet connection is detected and share files endpoint-to-endpoint when multiple user devices are connected to NordLayer.
Application-level security
They control user interaction with specific applications. As these services are very vulnerable to misuse by unauthorized users, the security measures must take into account the risks of the server and the client. Application security can include hardware, software, and procedures that identify or minimize security vulnerabilities. Application-level security is important because today’s applications are often available across multiple networks and connected to the cloud — increasing vulnerabilities to dangers and security threats.
Transmission-level security
They protect data communications that occur within the network and between multiple networks. If the data is not applied, it will be visible to anyone who wants to see and use it.
To deal effectively with internet threats and attacks and have comprehensive protection, the entire company must have a security policy that must be implemented together with the security strategy for each layer, as well as establishing how the interaction of the different strategies.