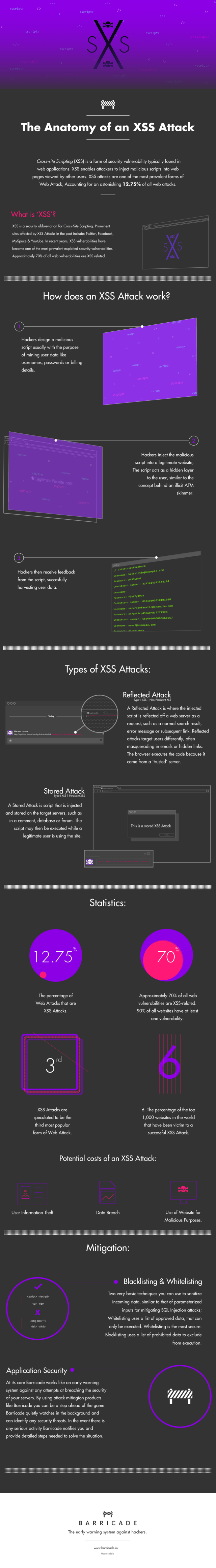
The Cross-Site Scripting or XSS attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. XSS attacks are one of the top three most prevalent forms of web attack. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end-user.
Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.XSS vulnerability may be used by attackers to bypass access controls such as the same-origin policy.
Here is a detailed infographic description of XSS attacks and XSS vulnerability from Barricade. Infographic will explain to you what is XSS attacks? and how does it happen ?. It also explains the different types of XSS attacks.
In Short : XSS Attacks
XSS attacks occur when:
- Data enters a Web application through an untrusted source, most frequently a web request.
- The data is included in dynamic content that is sent to a web user without being validated for malicious content.
The malicious content sent to the web browser often takes the form of a segment of JavaScript, but may also include HTML, Flash, or any other type of code that the browser may execute. The variety of attacks based on XSS is almost limitless, but they commonly include transmitting private data, like cookies or other session information, to the attacker, redirecting the victim to web content controlled by the attacker, or performing other malicious operations on the user’s machine under the guise of the vulnerable site.