After our previous post What is XSS attacks and how does it work?, today we are going to discuss about SQL Injection attack. SQL Injection attack is a technique where malicious users can inject SQL commands into an SQL statement, via web page input. SQL inject commands can alter the SQL statements and compromise the security of a web application. SQL injections are mostly known as an attack vector for websites but can be used to attack any type of SQL database.
The first public discussions of SQL injection started appearing around 1998. SQL injection (SQLI) is considered one of the top 10 web application vulnerabilities of 2007 and 2010 by the Open Web Application Security Project. In 2013, SQLI was rated the number one attack on the OWASP top ten. Recent infamous victims of SQL Injection Attacks: Barracuda Networks, Heartland Payment Systems, NASA, Bell (Canada) & Many More.
SQL Injection Attack Threat Modeling
SQL injection errors occur when data enters a program from an untrusted source and the data used to dynamically construct a SQL query
- SQL Injection attack allows attackers to spoof identity, tamper with existing data, cause repudiation issues such as voiding transactions or changing balances, allow the complete disclosure of all data on the system, destroy the data or make it otherwise unavailable and become administrators of the database server.
- SQL Injection is very common with PHP and ASP applications due to the prevalence of older functional interfaces. Due to the nature of programmatic interfaces available, J2EE and ASP.NET applications are less likely to have easily exploited SQL injections.
- The severity of SQL Injection attack is limited by the attacker’s skill and imagination, and to a lesser extent, defense in depth countermeasures, such as low privilege connections to the database server and so on. In general, consider SQL Injection a high impact severity.
Below infographic from Barricade will explain to you what is SQL Injection attack, how does it work.
Also Read : [Infographic] What Is Programming And What Do Programmers Do?
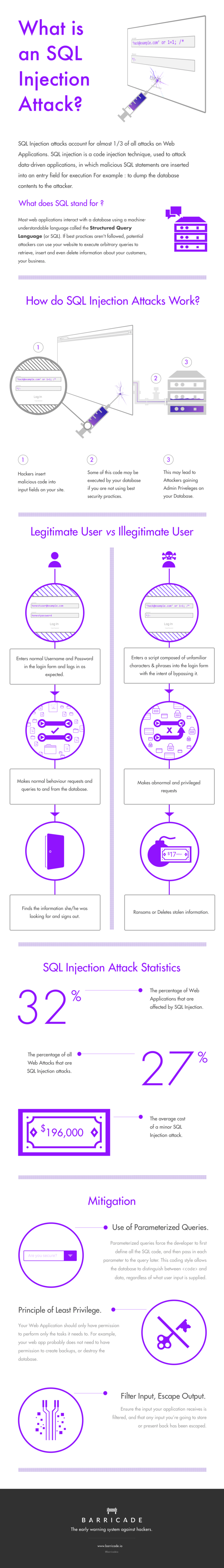
There are four different types SQL Injection attack, Classic SQLI, Blind or Inference SQL injection, Database management system-specific SQLI and Compounded SQLI. We will explain it in detail later. And we will also write an article about how to avoid SQL Injection vulnerabilities.