Believe it or not, someone just won £500,000 for solving one line mathematical equation, which remained unsolved for last 300-years. A professor from Oxford University earned this achievement by cracking Fermat’s Last Theorem.
Also Read : Stardock’s new multi-GPU tool let you mix AMD and Nvidia graphics cards in a PC
Professor Won £500,000 For Solving Fermat’s Last Theorem
Sir Andrew Wiles, 62, was awarded the Abel Prize by the Norwegian Academy of Science and Letters for his stunning proof of Fermat’s Last Theorem, which he published in 1994, by way of the modularity conjecture for semistable elliptic curves, opening a new era in number theory.
The Abel Prize is widely regarded as the Nobel for mathematics and the most prestigious international award for the discipline.
“It is a tremendous honour to receive the Abel Prize and to join the previous laureates who have made such outstanding contributions to the field.
“Fermat’s equation was my passion from an early age, and solving it gave me an overwhelming sense of fulfilment,” — Sir Andrew, currently a professor at Oxford University’s Mathematical Institute was quoted as saying by The Telegraph
“It has always been my hope that my solution of this age—old problem would inspire many young people to take up mathematics and to work on the many challenges of this beautiful and fascinating subject.”
Also Read : New MIT Javascript code will load all web pages 34% faster in any browser
First formulated by the French mathematician Pierre de Fermat in 1637, the Fermat’s Last Theorem states: There are no whole number solutions to the equation xn + yn = zn when n is greater than 2. Wiles has been awarded for developing proof for this simple looking yet complex theorem.
Fermat himself claimed to have proved the theorem, but in what must rank as one of the greatest teases in the history of mathematics, claimed that the margin of the book he was making notes in was too narrow to elaborate. Over the next three centuries, mathematicians around the world tried and failed to solve the theorem.
Wiles took seven-year quest to solve the problem, working in his attic without telling anyone except for his wife. In 1993, after seven years of intense study at Princeton University, Wiles went public with his proof in a series of lectures at Cambridge. When he wrote the proof on the board to conclude the lectures, the room erupted in applause from the two hundred researchers present.
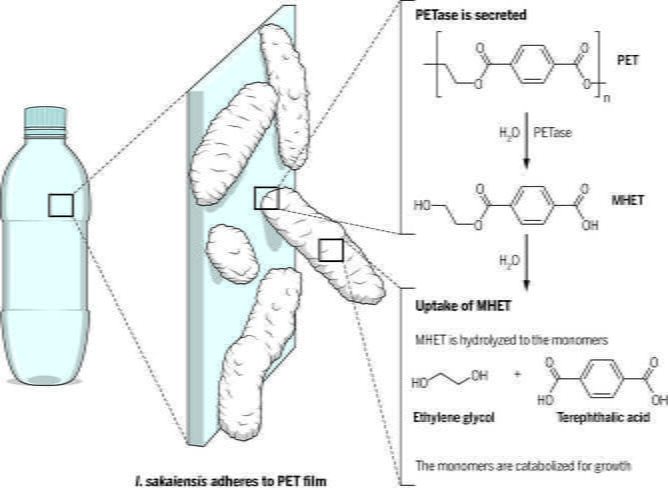
Also Read : Newly discovered plastic-eating bacteria could save our planet
But later that year, a mathematician who was checking Wiles’s proof found a major mistake in his workings. Wiles was devastated but vowed to fix the error, and called on his former student, Richard Taylor to help. After a year of work, the mistake was corrected and the revised proof published.
Wiles had solved the problem by combining three complex mathematical fields, namely modular forms, elliptic curves, and Galois representations. Though complicated, Wiles said the equations were not beyond the capabilities of a student. “The truth is the methods I used were not any more sophisticated than I could certainly do as an undergraduate,” he said.
In solving the Fermat’s Last Theorem, Wiles developed new tools which have since allowed researchers to make great strides in an ambitious effort to unify disparate branches of mathematics.
Also Read : Scientists Built Biological Supercomputer for Much Faster Problem Solving Using Very Little Energy