Google unveiled a new smartphones — named Pixel , at its annual autumn event, considered to be a high-end competitor to flagship devices like the iPhone and Galaxy S-series.
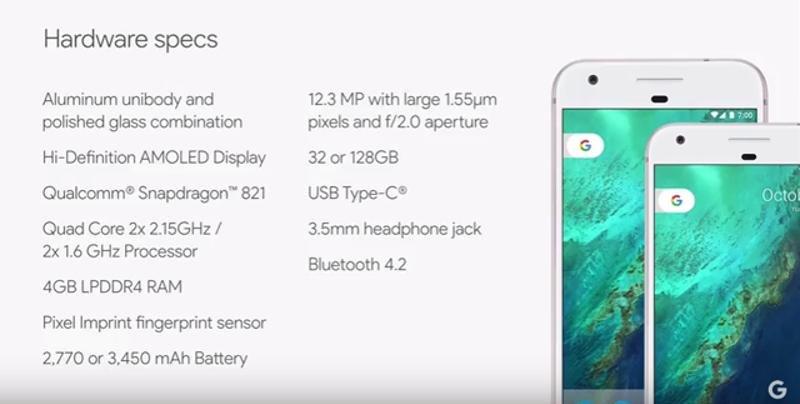
Starting at a price of Rs 57,000, the Pixel smartphones will come in two screen sizes — a 5.5-inch and a 5-inch variant. The phone will be available in two colours – Quite Black and Very Silver with memory configurations of 32GB and 128GB sizes.
Interestingly Pixel smartphones comes with the company’s artificial intelligence — Google Assistant, similar but much advanced one that we already saw in Google Allo messenger.
Also Read : Coming soon Andromeda OS — Google’s Android-Chrome OS hybrid
“Google is now moving forward from a mobile-first platform to an artificial intelligence-first platform. And the culmination of all the efforts is the Google Assistant,” Google CEO Sundar Pichai said, before he kicked off the keynote speech at Ghirardelli Square Fisherman’s Wharf area of San Francisco, California.
“The Assistant will help Google design a personal Google for everyone,” he added just seconds before announcing the launch of Google’s latest smartphones — Pixel and Pixel XL.
Device will run Android Nougat 7.1 with a tweaked aesthetic and claims to be the “best ever” smartphone camera, which is 12.3MP with an f/2.0 aperture. And also the device is protected by Corning Gorilla Glass 4, will come with Qualcomm Snapdragon 821 processor along with a 4GB DDR4 RAM unit. Other specifications include a 2770 mAh and 3450 mAh battery options, latest Bluetooth module, USB Type C and 3.5 mm headphone jack. The phones will also come with Google Duo and Allo pre-installed.
Google also launched its latest Chromecast device called Chormecast Ultra — supporting 4K content, which Google is going to roll out under Play Movies app, it promises superior image quality. The product will retail for $69 from November.
Also Read : Google planning to add Social Network features in YouTube to compete with Facebook, Twitter

The company also showcased network assisted Google wifi.Network assist works in the background to provide seamless connectivity. It also comes with an app which can control the routers for parental guidance. Google wifi will retail for $129 for single packs and $299 for larger homes and products will start shipping in December.

Another product Google launched at the event was Daydream VR headset comes along with a controller. The virtual reality headset and motion-sensing controller make use of Pixel – and other forthcoming compatible phones – as a display.
Also Read : Google is developing a new Open Source OS that’s not based on Linux

Another major launch was a smart wi-fi speaker — Google Home, which will activate by the trigger words “OK Google“, following which, owners can use it to : get answers to questions,control internet-connected lights and other smart home products,play music via Spotify, YouTube Music, Google Play Music and other services,set timers and alarms, create shopping lists and get travel updates.

However, Google Home, wifi and Daydream VR headset may not be available in India soon. The Chromecast Ultra is expected to come to India soon. The company has not yet announced India prices for any of this products.
Also Read : Google introduced ‘Project Bloks’ to teach kids how to code