Hacking attacks that comes from bootkit malware is one of the hardest security threat to resolve, for trained professionals. Even wiping your harddrive and reinstalling software will not fix them. And the company Dell just realized it and going to provide an extra a layer of security to its business laptops and PCs by introducing a new BIOS security tool which helps to protect the BIOS from malware.
Also Read : NSA Chief Hacker Explains How To Avoid NSA Spying
LogBook : Dell’s New BIOS Security Tool
Many manufactures are offering a number of ways to protect the computer BIOS, but all of these protections reside within the computer itself.
Now Dell introducing a new BIOS security tool that will protect the BIOS from attacks by verifying it without relying on the integrity of the PC. So the new Dell BIOS security tool focuses on protecting the boot layer so PC hardware or software don’t malfunction.
It secures the low-level UEFI (Unified Extensible Firmware Interface), which sits in a protected layer above the OS. An attack on this firmware can compromise a system at boot time.
The BIOS verification technology “gives IT the assurance that employees’ systems are secure every time they use the device,” said Brett Hansen, executive director of data security solutions at Dell.
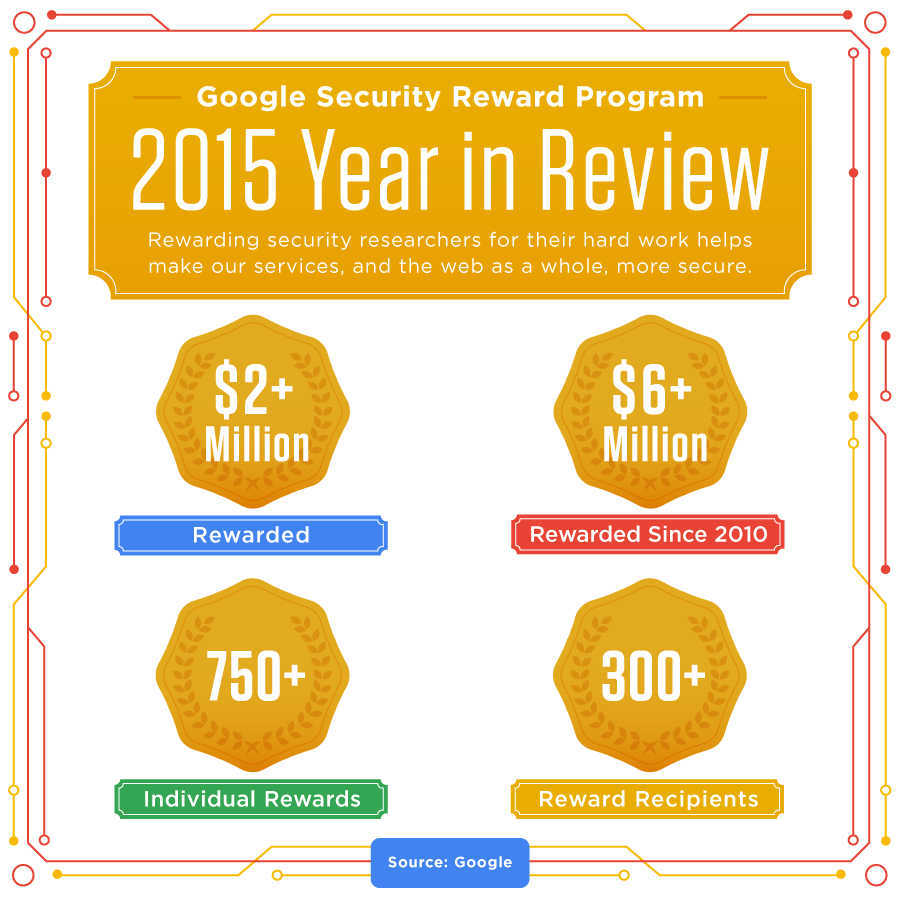
Also Read : Google Has Rewarded Over $6 Million To Security Researchers Since 2010 For Finding Flaws
How New BIOS Security Tool Works
This new tool makes a copy of the clean UEFI which is kept in the cloud, and compares this snapshot with the machine’s UEFI every time it boots.
If something’s been hacked or messed with, there’ll be a discrepancy between the two which the comparison will flag up.
The user or admin can then be notified of the problem, and the system subsequently reverted to the clean UEFI.
That will still have to be done manually at this point, but in the future Dell aims to automate the entire process.
The system will be optional, and will cost extra for users who decide they’d like this level of protection.
The new functionality is available for commercial PCs with a 6th-generation Intel chip set and a Dell Data Protection | Endpoint Security Suite Enterprise license, which includes Latitude, Dell Precision, OptiPlex, and XPS PCs. The technology would also be available for Dell Venue Pro tablets.
Intel already provides system management tools to protect the boot layer in PCs. System administrators can remotely start a PC, fix the boot layer, and then shut down the PC. HP also includes secure boot tools in its business PCs, though they are designed for individual users.
Also Read : Skype Now Hides IP Address By Default In PC And Mobile