In case you have somebody you need to know better, and for that, you should approach their instant messages. Yet, there is no application on your mobile phone device to take care of the work. You don’t need to enlist a spying app.
In light of everything, there are a couple of web-based spying applications accessible in the market today; this guide can help you with that.
Before picking any such application, ensure it accommodates your necessities consummately. The best spying application you can employ as your mystery analyst is Minspy. It has got all the best spying application highlights, including mystery and no application establishment components.
Minspy
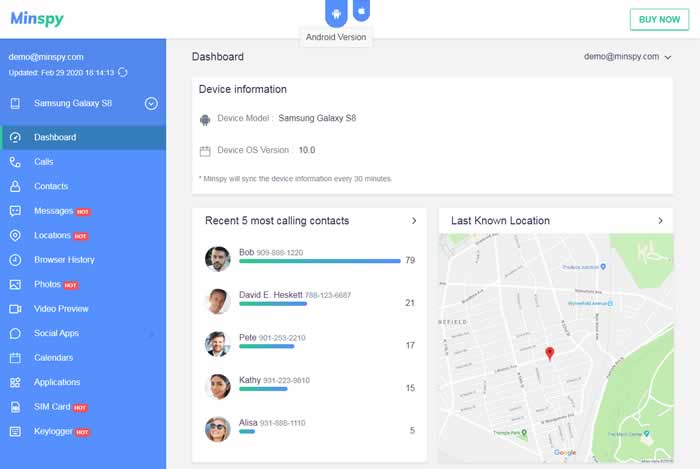
Minspy is in a real sense helps you read someone’s text messages like your own personal analyst. It offers to peruse the messages distantly, from both android and iPhones. You shouldn’t be genuinely in contact with the gadget. Minspy has got a great many cheerful surveys in its record.
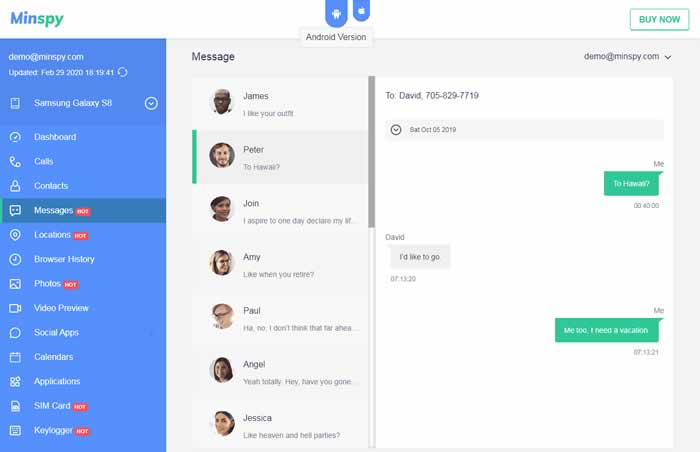
Minspy resembles an all-inclusive resource where you can peruse somebody’s instant messages by Minspy without contacting that gadget alongside messages from various web-based media accounts.
With Minspy, it’s not merely the instant messages you can peruse. It can show you any message that the objective mobile phone device sends and gets by utilizing any web-based media stage. Minspy is lightweight and consumes just 2M space in the objective gadget.
This article educates you that for iOS gadgets, it is viable with form 7.0 or later. For Android devices, ensure your better half’s mobile phone device is 4.0 or more.
What Makes Minspy The Best Spying Application?
First thing first, regardless of whether you are a ceaseless tyro in regard to innovation, you can at present utilize Minspy like a star. Unlike a spying application, you find it in films. Minspy is an expert instant message spying app that needn’t bother with any establishing or jailbreaking.
This is fundamental because of its exceptional forefront advancements. It needn’t bother with any download or establishment in Apple gadgets to keep an eye on his messages.
Nonetheless, for Android gadgets, you have to introduce Minspy only once on the mobile phone device. Ensure you initiate covertness mode so your better half won’t presume anything.
In the event that the individual you’re keeping an eye on is somebody you care about, at that point, don’t stress over the security. None of your private information is put away on Spyine own workers; in Minspy, you don’t need to root or escape the objective mobile phone device.
Minspy works in secrecy mode and can take a shot at both Android and iPhone gadgets. You can utilize Minspy from its web dashboard that opens in any internet browser that you use. For the iPhone variant, there is no compelling reason to introduce any application. Minspy utilizes the iCloud reinforcement to remove all the data.
How To Set Up Minspy On Target Device?
Step insightful manual to read somebody’s instant messages through Minspy:
For iPhone
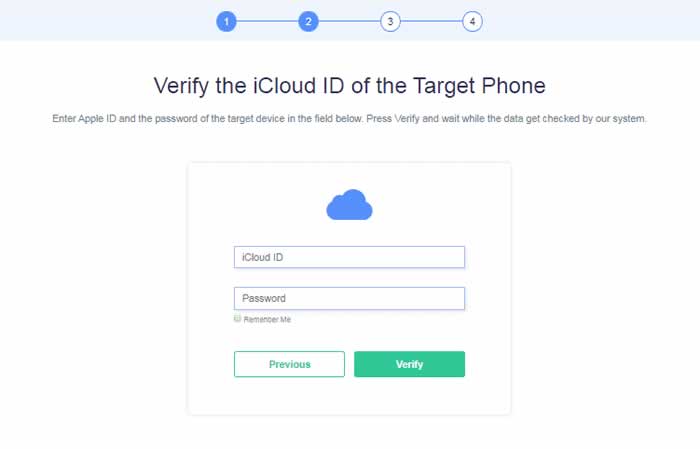
- The initial step is to go to the official site and make a record. It would be best if you bought in for an arrangement to begin utilizing Minspy by paying a little measure of cash.
- For an iPhone, you need to remember the iCloud accreditations so you can utilize them whenever you need to keep an eye on an iPhone.
- The final advance is to hit the ‘start’ catch, and you have recruited your computerized spy.
- After that, you will arrive at your dashboard, where you can utilize various highlights like keeping an eye on web-based media accounts, instant messages, call history, and program history.
For Android
- The initial step is the equivalent: you need to make a Minspy account and get a membership plan for android gadgets.
- Download and introduce the Minspy application on track mobile phone devices. The application won’t be evident in the objective gadget.
- Hit the ‘start’ catch and rest aside.
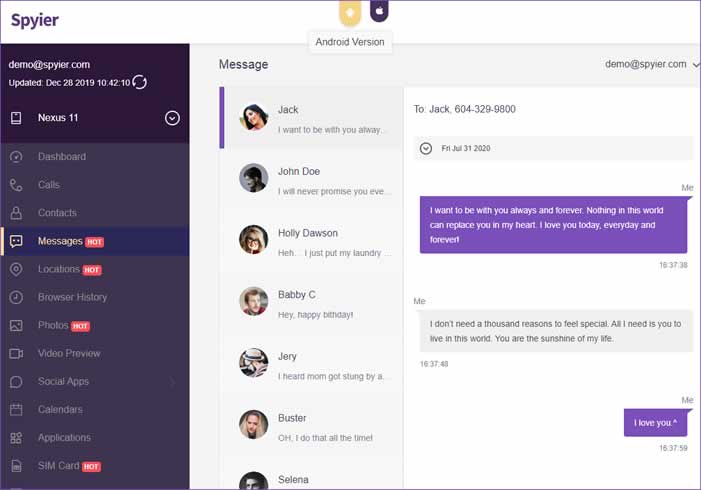
Spyier
The cool thing about a Spyier is its interface, which is arranged towards convenience. Spyier, as Minspy, is a web administration that works without escape on both android and iPhone. Spyier has its group of clients upholding chiefs that are anxious to help you with any issue you may confront.
Spyier is light on the wallet. All the highlights can be utilized from a solitary screen dashboard with a devoted tab on each element’s left-hand corner.
Spyine
Spyine is less famous than Minspy and spyier. Yet, the claim to fame of Spyine lies in its web-based media informing arrangement. On the off chance that you need to keep an eye on any web-based media application like WhatsApp, Facebook, Instagram, and Snapchat. Spyine is your best accomplice for following all the messages of these stages. With Spyine, you can even peruse the erased messages.
It is a program based on you and login subsequently from anyplace utilizing any gadget to keep an eye on messages.
It would be best if you actuated covertness mode by picking the ‘shroud application’ choice when introducing on android. For iOS gadgets, it is programmed. In your online record, Minspy will catch all the sent and received messages.
Utilize the inbuilt message module to see the approaching and friendly messages alongside the individual subtleties of the client’s individuals. With the keylogger included, you can discover anything the client has composed.
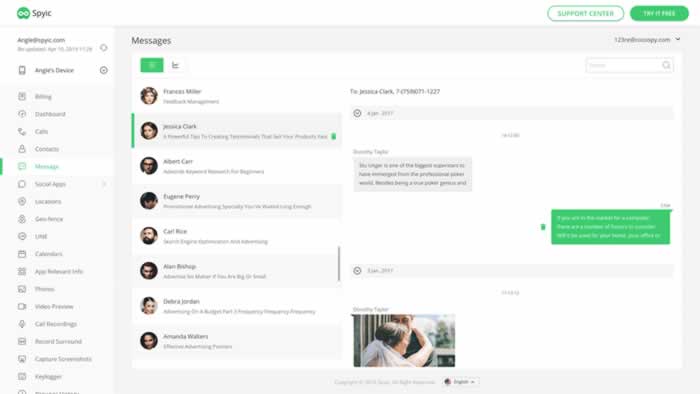
Spyic
In the event that you are stressed over your youngster investing a lot of energy in mobile phone devices. Spyic is the best answer for you. You can approach your youngster’s instant messages, Social media records, and program history without uncovering your character. Spyic takes a shot at both iPhone and Android gadgets. It works out of sight and takes almost no space.
You can cover up the application, and there is no installation required. Hence, it is implausible your kid can think about it. In the event of the iPhone, there is no compelling reason to contact the mobile phone device.
Simply remember the iCloud qualifications and use it however long you need. You can uninstall the application distantly if there should arise an occurrence of android on the off chance you need to quit following your youngster.
With Spyic, you would now be able to easily keep an eye on your significant other’s instant messages. It’s likewise a concrete, spying application that has a great many clients.
It is viable with all programs as long as you have a web association. You can utilize Spyic on both android and iOS. The best thing about it is that you can uninstall it distantly in your online record.
Neatspy
Neatspy is instant message spyware that has additionally stood out as truly newsworthy in enormous news sources like CNET and PC World. It doesn’t store the data subsequent to spying. All things being equal, it utilizes its cloud as a spot to synchronize the data you get.
The Bottom Line
On the off chance that you need to check somebody’s instant messages without uncovering yourself and contacting the gadget, you can do this by utilizing any of the strategies depicted previously. The best one is Minspy due to its multi-highlights and easy-to-use administrations.
Presently, it’s dependent upon you to follow the means and see the individual’s mobile phone messages on your screen inside merely five minutes.