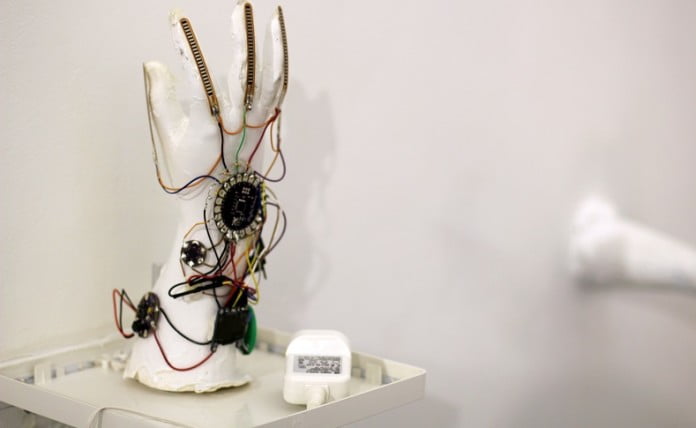
Researchers of Novel Electronics Group at PARC, a Xerox company has developed a new tempered glass-made computer chip can self destruct in 5 seconds. Researchers says that this new technology can keep sensitive date more secure than before because computer chip can self destruct in 5 seconds when remotely triggered. The chip was put on display at the DARPA organised ‘Wait, What? Technology Forum’ in St. Louis.
The chip uses silicon computer wafers integrated with a piece of tempered glass. This glass can be breaks into small pieces when heated in one spot. Gregory Whiting, a materials scientist and manager of the Novel Electronics Group that produced the chip at California-based PARC company, said, the heat can be turned on using a remote that could conceivably be triggered by anything from Wi-Fi to a radio-frequency signal. The new technology could allow for easier recycling of electronics, or help ensure that data on stolen electronics remains secure, Whiting said.
Whiting told Live Science that the team was initially aim to use off-the-shelf products to create self-destructing chip. Then the researchers considered a number of methods of destruction, from vaporization to dissolving before finalizing with the tempered glass.
Also Read : A Smart Glove That Translates Sign Language Into Text And Speech

The team came upon the idea of tempered glass, an extra strength material also known as safety glass. Normally, people temper glass by cooling the edges: The glass exterior shrinks, putting the exterior into compression while the warmer interior maintains incredible tensile stress. Though the glass is stronger than normal.
“if you break a piece of safety glass, it kind of explodes, shatters explosively into little pieces,” — Whiting said.
Also Read : Aston Martin Racing 808 Smartphone Is The Phone James Bond Should Have
As glass is a poor temperature conductor, the heat-tempering process takes place only pieces of glass that are at least 0.03 inches thick, whereas producing tiny particles requires thinner materials.
To temper the glass the team came forward with a new method called ion exchange. The researchers started with a thin piece of glass that was rich in sodium ions, or atoms of sodium with one electron stripped off. They then put the glass into a hot bath of potassium nitrate. Potassium ions then try to swap places with the sodium ions, but because the heftier potassium ions must squeeze into place within the silicon matrix, this creates enormous tension in the glass, Whiting said.
Also Read : Pakistani Researchers Developed Solar-Powered Emergency Mobile Network
The new method lets the chip makers to put silicon wafers directly on the glass, and the resulting product looks like a piece of glass with thin metallic lines. In order to destroy the chip, the team triggers the chip with a tiny heating element, which causes a thermal shock that creates a fracture that spreads throughout the glass. The current demonstration uses a piece of glass that is 250 micrometers thick, but theoretically, any size glass could be used, Whiting said.
The new technology of computer chip can self destruct in 5 seconds provide an extra advanced layer of protection to sensitive data because the self-destruction technique not only erases all the data from the chip but also alters the tiny bits that make it almost impossible to put together.
Also Read : Samsung’s Dual-Screen Foldable Smartphone Might Launch In January



![Aston Martin Racing 808 smartphone [TechLog360.com] Aston Martin Racing 808 smartphone](https://tl360.b-cdn.net/wp-content/uploads/2015/10/Aston-Martin-Racing-808-smartphone-TechLog360.com_-696x483.jpg)


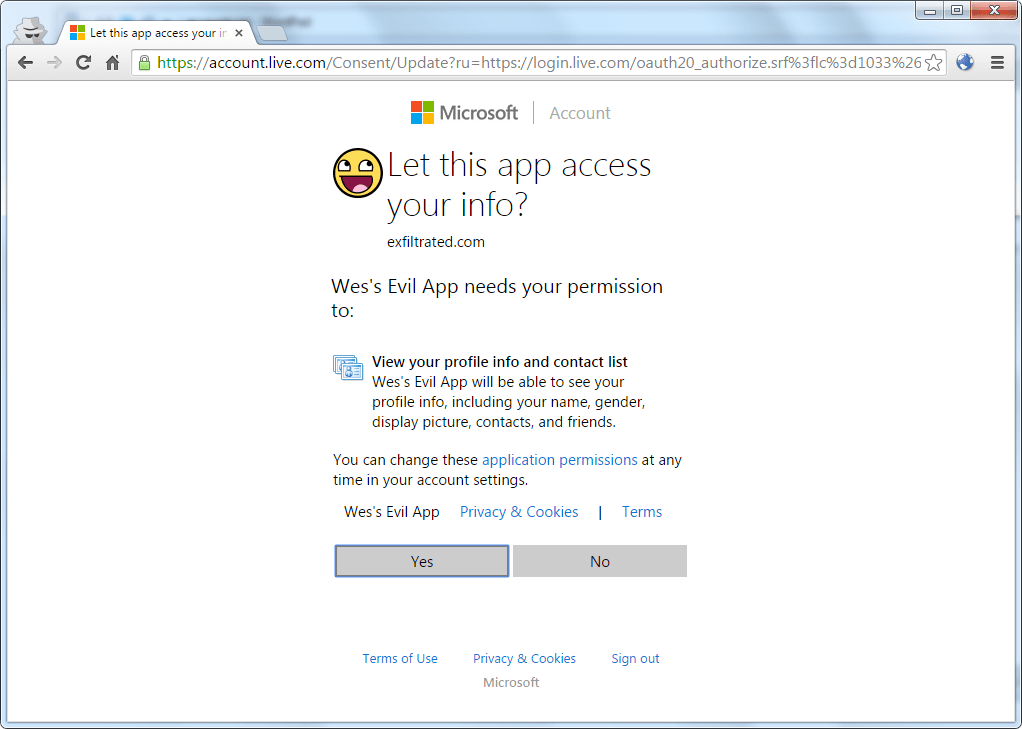
![hacking outlook account [TechLog360.com] hacking outlook account](https://tl360.b-cdn.net/wp-content/uploads/2015/10/hacking-outlook-account-TechLog360.com_-696x342.jpg)

![Tim Berners-Lee [TechLog360.com] Tim Berners-Lee says no to internet.org](https://tl360.b-cdn.net/wp-content/uploads/2015/10/Tim-Berners-Lee-TechLog360.com_.jpg)