The railroad in India are known as ” The Lifeline to the Nation ” is soon going to become Wi-Fi line of the Nation. In a blogpost Google announced that as the part of Digital India initiative Google is going to provide high-speed public Wi-Fi connectivity in 400 train stations across India by the end of 2016.
At first [p2p type=”post_tag” value=”google” attributes=”target=’_blank'”]Google[/p2p] is planning to put to high-speed Wi-Fi connectivity in 100 of the country’s busiest stations by the end of 2016, and it hopes to eventually bring connectivity to 400 stations in total. Those 100 initial stations serve over 10 million riders a day, according to the search company.The initiative, which will be accomplished together with Indian Railways and provider RailTel, was announced yesterday during an event at Google’s Mountain View campus with Indian Prime Minister Narendra Modi. He’s been visiting influential Silicon Valley companies, including Facebook, over the past few days.
Also See : [p2p type=”slug” value=”pakistani-websites-got-hacked-by-indian-hackers” attributes=”target=’_blank'”]More Than 50 Pakistani Websites Got Hacked By Indian Hackers As A Revenge For Hacking Kerala Govt. Website[/p2p]
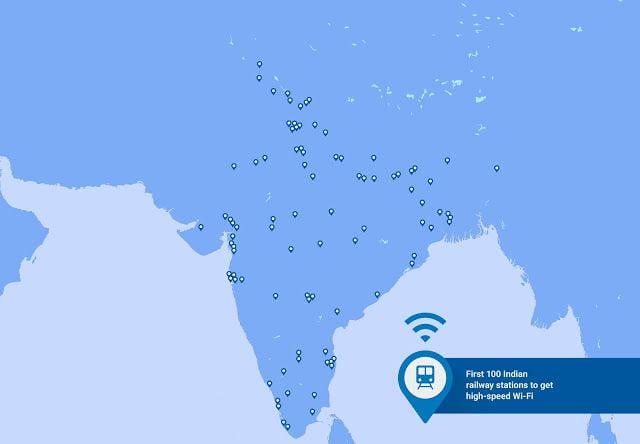
After China, India have more Internet users. And this project will be will make Wi-Fi available for the more than 10 million people who pass through every day. This will rank it as the largest public Wi-Fi project in India, and among the largest in the world, by number of potential users. It will also be fast—many times faster than what most people in India have access to today, allowing travelers to stream a high definition video while they’re waiting, research their destination, or download some videos, a book or a new game for the journey ahead. Best of all, the service will be free to start, with the long-term goal of making it self-sustainable to allow for expansion to more stations and other places, with RailTel and more partners, in the future.
Also See : [p2p type=”slug” value=”indian-it-firms-are-one-of-the-top-10-worst-paymasters-in-the-world” attributes=”target=’_blank'”]Indian IT Firms Are One Of The Top 10 Worst Paymasters In The World[/p2p]
Other than this Google also provide many service to access internet is more smarty and affordable way, last year they launched Android One smartphones . To help address the challenges of limited bandwidth, Google recently launched a feature that makes mobile webpages load faster and with less data, and also YouTube available offline with offline Maps coming soon. And for those who don’t speak English, they launched the Indian Language Internet Alliance last year to foster more local language content, and have built greater local language support into our products—including Hindi Voice Search, an improved Hindi keyboard and support for seven Indian languages with the latest versions of Android.
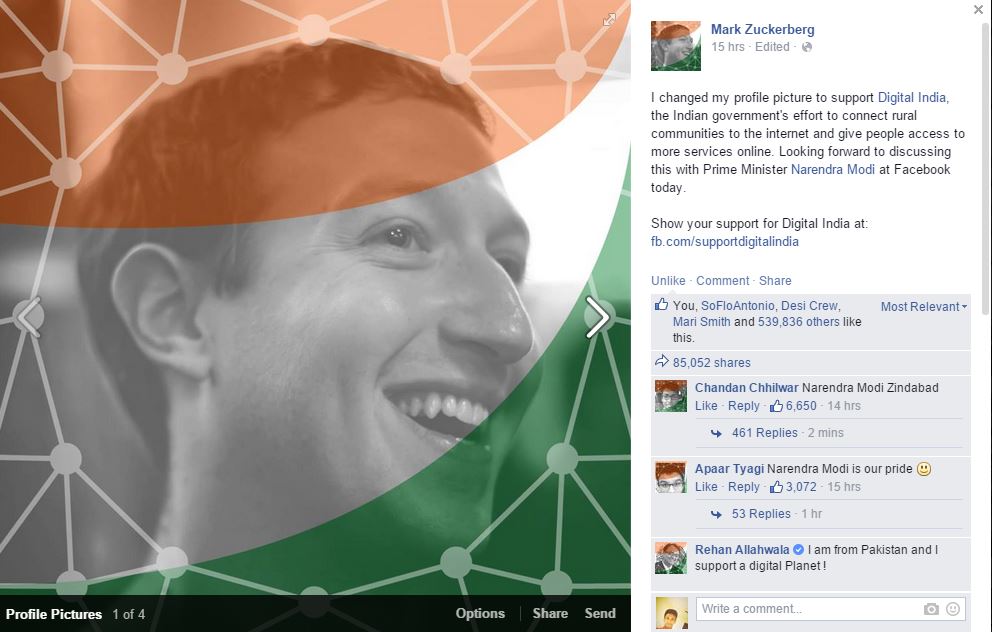
Since Digital India initiative is really trending in social networks in last two days. Yesterday Facebook CEO Mark Zuckerberg show his support to Digital India by changing his profile picture.
Also See : [p2p type=”slug” value=”indian-scientists-developed-a-new-algorithm-to-prevent-cybercrime” attributes=”target=’_blank'”]Indian Scientists Developed A New Algorithm To Prevent Cybercrime[/p2p]


![modi-sundar [TechLog360.com] modi-sundar](https://tl360.b-cdn.net/wp-content/uploads/2015/09/modi-sundar-TechLog360.com_-696x516.jpg)











![emoji keyboard [TechLog360.com] emoji keyboard](https://tl360.b-cdn.net/wp-content/uploads/2015/09/emoji-keyboard-TechLog360.com_-696x522.jpg)
![taking selfies [TechLog360.com] taking selfies](https://tl360.b-cdn.net/wp-content/uploads/2015/09/taking-selfies-TechLog360.com_.jpg)
![iOS 9 [TechLog360.com] iOS 9](https://tl360.b-cdn.net/wp-content/uploads/2015/09/iOS-9-TechLog360.com_-696x392.jpg)
![candy crush [TechLog360.com] candy crush](https://tl360.b-cdn.net/wp-content/uploads/2015/09/candy-crush-TechLog360.com_-696x500.jpg)
![rescue base station [TechLog360.com] rescue base station](https://tl360.b-cdn.net/wp-content/uploads/2015/09/rescue-base-station-TechLog360.com_-696x366.jpg)
