Every state has multiple information centers where you can ask for someone’s information legally. However, most people do not have enough time to visit those centers to get this information. Additionally, there are times when you do not want to disclose your identity while asking for someone’s personal information.
When you are getting into a new relationship or dealing with a new client, it can cause similar scenarios. Hence, you need an effective platform to find that information without them knowing.
Today, we will discuss five easy ways to find out someone’s information online. The best thing about them is that they can be accessed from your web browser and does not require any registration to proceed. So, let’s find out about these applications and learn how you can use them.
Tip: You can also check the best phone number lookup service reviews here.
Contents
Information.com
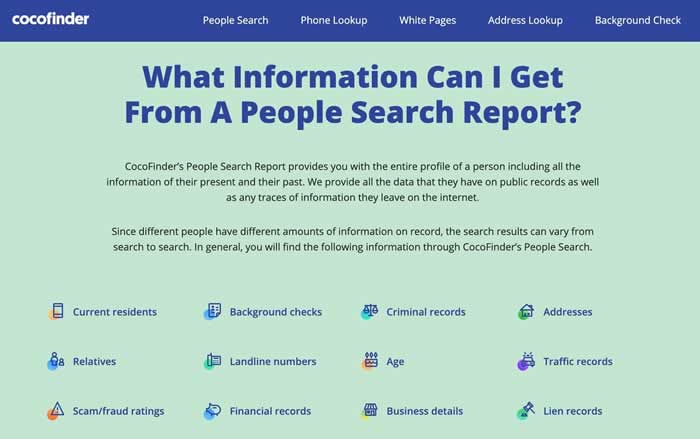
Information.com is one of the best places to go when you are searching for more information on someone. Their people search tool is straightforward to use – just type in their first and last name, as well as their city, and you’ll get a list of all the matching results. Click on the result you want to dive into, and you’ll get all the information you could need about them.
Not only is Information.com simple to use, but it’s also far more powerful than most other people searches available. First of all, it pours through massive amounts of public records related to the person you’re searching – including their criminal records, current and past addresses, phone numbers, email addresses, marriage records, and even their sex offender status.
But more impressively, Information.com goes beyond the standard public records results and also shows you what their powerful internet search finds out. This includes all the social media profiles attached to a person (including ones they’ve created under secondary emails or phone numbers), and even their dating profiles.
If you want to find out the complete picture of who someone is, Information.com is the perfect tool to use.
CocoFinder
CocoFinder is a public search engine to search for people and public information right from your device. This application is one of the most popular search engines as it contains accurate information about every individual. Additionally, there are many filters to help you find the information quickly.
CocoFinder’s website has multiple tools to help you know everything about someone’s life. It includes a background check, phone number lookup, white pages, and people search. Hence, you do not need to use any other application to get the complete background data of an individual.
The search allows you to enter the First and Last name of the person. After that, you can filter the results based on cities and areas to get accurate information.
How does it work?
Being a search engine, CocoFinder searches for information on the relevant information centers. When a person enters someone’s details, it shows the relevant data from its sources. It has the biggest database of personal information across online platforms.
Hence, you can trust this application to get results within a few seconds. You can visit its website to use the advanced tools along with the user guide.
ZabaSearch
ZabaSearch is a new yet effective solution to look for public information online. The best thing about this platform is that you can search for someone’s social media photos on it as well. Additionally, it has a separate feature to search for contact information of people that you want to connect with.
From someone’s age to job history, you can search for all the public information on this website. On top of that, there is an exclusive feature to help you perform a complete background check of any person you want.
If you are someone with privacy issues, then you must check out this application. It does not require any login or sign-up and works without collecting your personal information. Additionally, their website is encrypted with an SSL certificate to protect your identity from third-parties.
Note: Please read their privacy policy before using the social media handles feature of this website. It is because some states have different rules regarding this feature.
TruthFinder
The name of these applications makes its work quite clear. TruthFinder is another search engine that allows you to look for someone’s information anonymously. Like the previous websites, there is no need to register or sign up on this website as well. You can simply use its features and enjoy unlimited access to the public information of individuals across different states.
We like the fact this application offers different features for all your needs. It means that you can use the reverse phone lookup feature to know the owner of a number. After that, you can use that name to get other details about the same person. That way, you get complete access to someone’s information even with minimum source information.
You can also the advanced filters of this website to search for people across different states.
Instant Checkmate
If you are in a hurry and require a faster solution, Instant Checkmate is the website for you. It offers the fastest services to get someone’s public information from reliable sources. The database of this website is extracted from some of the most credible sources. Hence, you can trust it for a complete background check of a person.
Although it is a complete public information search engine, it is popular for its reverse phone lookup services. It allows you to know the information of an unknown caller by entering the phone number. Additionally, its advanced search can gather information about Virtual phone numbers as well.
Hence, you no longer need to worry about the telemarketers who use virtual numbers to call you.
Intelius
Intelius is another excellent solution to get someone’s information from the slightest clue. If you are receiving some callers from unknown numbers, you can use its phone lookup service. Additionally, there is a background check feature to help companies hire the right employees for the job.
You can find all the previous features on this website. The only difference is that the data is taken from the police records and is much more reliable than others. That is the reason why most of the companies prefer to use this application in their hiring process.
You can visit its website to learn more about the features and working of this application.
Final Words
After going through these websites, you will get all the information you are looking for. CocoFinder and Zabasearch are two excellent platforms to perform a background check. By just entering someone’s full name, you can check their criminal history, court sessions, and parking ticket history remotely.
You can also protect your identity as there is no need to register on the above websites. All you need is to visit these websites and search for all the information you need. However, you must remember that this data must not be used for illegal purposes. Hence, it is recommended to go through the privacy policy of these websites for legal reasons.