You’re surfing the internet, scrolling through social media, or perhaps doing some online shopping. It all seems so straightforward, right? But what if I told you that the internet is like an iceberg, and you’re merely skimming the surface?
Did you know only about 4% of the internet is accessible through search engines like Google and Bing. The remaining 96% of web content is only accessible with special tools and software — anonymous browsers and other protocols beyond direct links or credentials.
The internet is a vast, intricate landscape with multiple layers, each serving a unique purpose and audience. In this article, we’ll guide you through a journey into the lesser-known realms of the World Wide Web: the Surface Web, the Deep Web, the Dark Web, and the Darknet. Prepare to uncover the mysteries that make up the internet’s complex ecosystem.
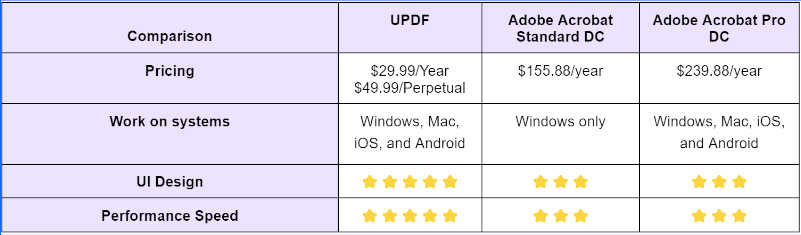
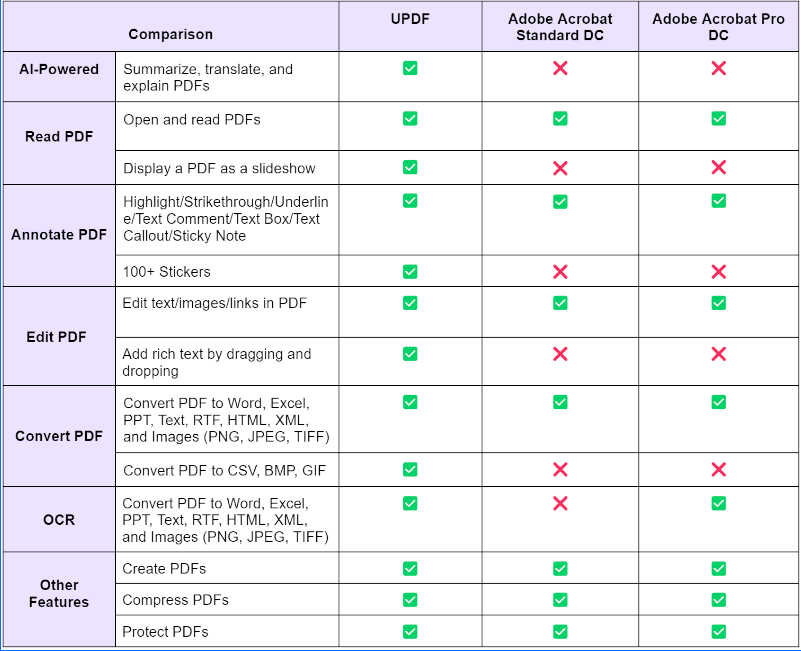
Quick Reference Guide:
| Feature/Aspect | Surface Web | Deep Web | Dark Web | Darknet |
|---|---|---|---|---|
| Accessibility | Easily accessible | Requires login or subscription | Special software needed (e.g., Tor, I2P) | Invitation and special software required |
| Search Engines | Indexed by Google, Bing, etc. | Not indexed | Not indexed | Not applicable |
| Content | Public websites, blogs, forums | Academic databases, private data | Illegal activities, political activism | Private networks, often encrypted |
| Anonymity | Low | Moderate | High | Very High |
| Legal Status | Legal | Mostly legal | Mix of legal and illegal | Legal but can be used for illegal activities |
| Percentage of Web | About 4% | Approximately 90% | Less than 1% | Not quantified |
| Examples | Facebook, Wikipedia, News sites | Medical records, academic journals | Silk Road, whistleblower sites | Private P2P networks, some parts of Dark Web |
| Primary Use | General browsing, information | Research, private transactions | Anonymity, often illicit activities | Highly secure, anonymous communication |
Surface Web
The Surface Web is just the tip of the iceberg in the grand scheme of the World Wide Web. It’s the part of the internet that’s indexed by search engines like Google and Bing. These search engines use algorithms to crawl through web pages, indexing them so they can be easily found by users. This is the realm of the internet where Search Engine Optimization (SEO) reigns supreme. Companies and individuals alike compete for the coveted first-page search results, employing a myriad of tactics from keyword stuffing to backlinking.
Moreover, the Surface Web is also the most monitored and regulated part of the internet. Government agencies, corporations, and hackers can track your activities with relative ease. Cookies follow you around like digital breadcrumbs, helping (or haunting) your online experience by tailoring ads specifically for you. And let’s not even get started on data collection and privacy concerns.
Although the Surface Web is highly diverse with the bustling marketplace of ideas, products, and services, and yet, despite its vastness, it is just a small slice of the internet pie. Estimates suggest that it makes up only about 4% of the total internet.
Deep Web
The Deep Web is a repository for all things not indexed by traditional search engines. This includes academic databases like JSTOR, private social media posts, online banking accounts, and subscription-based platforms like Netflix or premium news outlets. Even your personal email account resides in the Deep Web.
Contrary to the ominous tone often associated with its name, the Deep Web is not inherently illegal or immoral. In fact, it serves as a vital function in preserving privacy and housing information that shouldn’t be readily available, such as medical records or confidential business documents.
Accessing the Deep Web isn’t as mysterious as you might think. You do it every time you log into your email account, check your online bank statement, or access a digital library. Specialized search engines and databases like DuckDuckGo or the academic database PubMed can also serve as gateways to this hidden realm.
The Deep Web is the backbone that holds vast amounts of critical, private data that is essential for the functioning of businesses, governments, and individuals. Understanding its scope and how to navigate it is crucial for digital literacy, online privacy, and cybersecurity.
Dark Web
The Dark Web is often portrayed as a digital Wild West, a lawless frontier teeming with outlaws and shady characters. While it’s true that the Dark Web can be a haven for illegal activities — think drug trafficking, arms sales, and even human trafficking.
Access to the Dark Web requires specialized software, most commonly Tor (The Onion Router) or I2P (Invisible Internet Project). These tools anonymize your online presence, making it difficult for anyone to trace your activities back to you. This level of anonymity is what sets the Dark Web apart from its more accessible counterparts.
Contrary to popular belief, not everyone on the Dark Web is a criminal. In fact, the Dark Web serves as a refuge for political dissidents, whistleblowers, and journalists who operate in countries with oppressive regimes. Edward Snowden, for instance, used the Dark Web to leak classified information about the U.S. government’s surveillance programs.
The Dark Web has its own economy. Websites with .onion extensions act as marketplaces for both legal and illegal goods. You can buy anything from rare books to pharmaceuticals, but remember, the lack of regulation makes it a risky venture. Cryptocurrencies like Bitcoin and Monero are the currencies of choice, further enhancing the anonymity of transactions.
It’s also worth noting that the Dark Web is a hotbed for hackers. Cybersecurity threats like ransomware often originate from this space. Forums exist where hacking tools and stolen data are bought and sold. Therefore, if you venture into the Dark Web, robust cybersecurity measures are not just advisable; they’re essential.
Lastly, the Dark Web is not a static entity. It’s constantly evolving, with websites appearing and disappearing like phantoms. Law enforcement agencies worldwide are working tirelessly to shut down illegal activities on the Dark Web.
Darknet
Darknet is not a place but rather a way of connecting. It’s a network within a network, a secure haven that operates under the radar of mainstream internet traffic.
The Darknet employs unique protocols and technologies to create a private, encrypted space. Unlike the Surface Web, where your IP address is an open book, the Darknet uses onion routing or other anonymizing techniques to mask users’ identities. This is achieved through specialized software like Tor or I2P. These tools route your internet traffic through multiple servers, encrypting it at each step, making it exceedingly difficult to trace. The Darknet provides a level of privacy and security that the Surface Web simply cannot offer.
Like the Dark Web, Darknet also hosts illegal activities. One of the most infamous aspects of the Darknet is its marketplaces. Sites like Silk Road have gained notoriety for facilitating the trade of illegal goods. However, it’s worth noting that these markets are just a small fraction of what the Darknet offers. There are also forums for political discourse, libraries of academic papers, and even social networks that prioritize user privacy.
Wrapping Up
The internet is a complex ecosystem with layers that go far beyond our daily Google searches. Understanding these layers is crucial for online privacy and cybersecurity. So the next time you log on, remember: there’s a whole hidden world out there, waiting to be explored — or avoided.