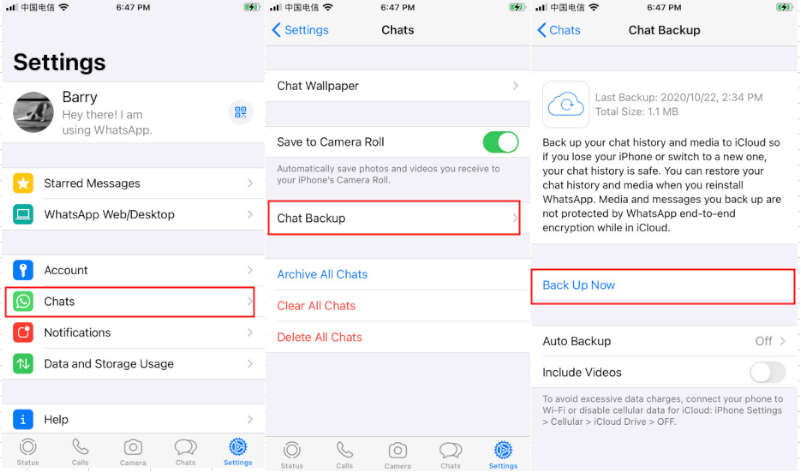
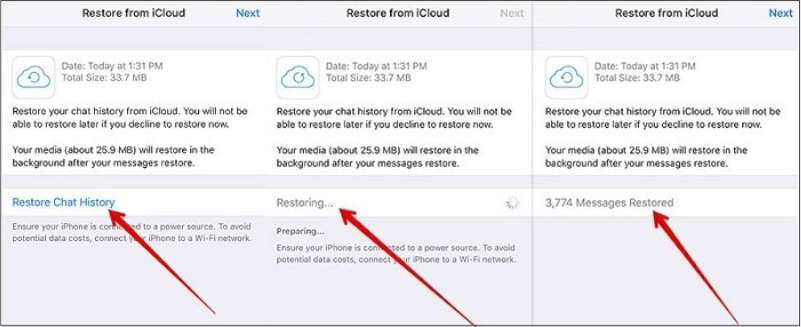
Keeping a building secure is an important part of managing any type of property. With the continued advancement in access control technology, it has become easier and more effective to protect buildings from unauthorized entry.
From keyless entry solutions to biometric authentication technologies, there are many options available for keeping buildings safe and secure. In addition, mobile-based access control systems offer greater flexibility when it comes to granting or denying access. Cloud-based security management platforms provide another layer of protection by allowing administrators to monitor activity remotely.
Finally, emerging trends such as facial recognition and voice authentication are making their way into the mainstream market and further improving the security of buildings around the world.
- Overview of Access Control Technology
- Benefits of Access Control Systems
- Types of Access Control Systems
- Keyless Entry Solutions for Buildings
- Biometric Authentication Technologies for Buildings
- Mobile-Based Access Control Technology
- Cloud-Based Security Management Platforms
- Emerging Trends in Building Security and Access Control Technology
Overview of Access Control Technology
Access control technology is a building security tool that helps businesses, organizations and individuals protect their premises. It uses various technologies, such as biometric scanners, keycards, control panels and magnetic locks, to manage who has access to different areas. The system allows you to assign access levels based on roles and other criteria. By using these technologies, you can restrict access to any building or area to safeguard people and assets from potential harm and unauthorized use. This type of building security also keeps unauthorized visitors away by providing an additional level of protection for the building occupants. With a combination of effective access control systems – such as camera surveillance, alarms and door locks – sites can be secured with confidence.
Benefits of Access Control Systems
Access control systems provide invaluable building security every day. From automated key fobs and card readers to digital cryptography, access control technology provides a non-transferable authorization process that grants building access. Other benefits of access control include easy tracking of building access information, limitation of building access to authorized personnel only, and improved accountability due to detailed records kept from each login. Access control systems are quickly becoming the go-to choice for building owners seeking enhanced security for their building occupants.
There are a variety of types of access control systems and technologies used in businesses today, each offering their own unique benefits.
Biometric Access Control Systems
Biometric Access Control Systems use biometrics to authenticate an individual’s identity with the help of fingerprint, iris, face scans, or voice recognition technology. These systems are considered one of the most secure types of access control available and are often used in high security areas where only authorized personnel should have access.
Keyless Entry Solutions
Keyless Entry Solutions are a type of access control system that uses RFID cards, keypads, or proximity readers to grant individuals entry into a building. This type of system is typically seen in residential buildings as it does not require physical keys and can be easily managed remotely.
Wiegand Access Control
Wiegand Access Control, named after its inventor John Wiegand, is an efficient building security system that can be used to control access to or within a building. It uses electromagnetic induction and current loop transmission techniques on co-axial cables or twisted pair wires, with three basic components – a stripe card reader, a controller and an access panel. The system works by transmitting card data such as birthdates, serial numbers and names from the access reader to the controller which then grants or denies building entry upon verification. Wiegand Access Control technology provides convenience for building occupants as it allows them to move within the building’s secured areas without needing to show their credentials like identification cards multiple times. It is also easy to use and maintain as its installation only requires basic wiring work. These features allow building owners and security personnel alike more time for other important tasks without having to worry about unauthorized building entries.
Mobile Access Control Technology
Mobile Access Control Technology is quickly emerging as one of the go-to security methods for many businesses, especially those that need secure access from outside their premises. Mobile access control systems can be controlled from any web-enabled device, giving greater flexibility to building managers who may have remote teams or multiple locations.
Cloud-Based Access Control Management
Finally, cloud-based access control management applications provide a convenient way for building administrators to track and manage user access from any device with an internet connection. Cloud-based systems are highly secure and offer many features such as real-time reports, user management tools, and automated notifications when changes occur.
As technology continues to evolve and advance, so too does the world of access control for buildings. The past few years have seen a surge in new trends and innovations as it relates to building security, allowing for greater levels of protection and convenience. Here is a look at some of the new trends in access control technology for buildings that are making waves in 2019 and beyond.
Smartphone-Enabled Access Control Systems
Smartphone-enabled access control systems are quickly becoming the go-to choice for businesses looking to modernize their security. These systems allow building administrators to manage user access from a single app, eliminating the need for physical keys or cards. This type of system also offers other benefits such as automated access management, real-time notifications, and a detailed audit trail.
Automated Access Control Systems
Automated access control systems are gaining popularity due to their ability to quickly identify and authorize users through facial recognition technology or RFID cards. These systems are especially useful for applications where there is high traffic flow, such as office buildings, hospitals, and airports. Additionally, they can also be used to manage access hours and monitor who has accessed specific areas of the building.
Integrated Security Systems
Integrated security systems offer a comprehensive approach to access control by combining multiple security technologies such as CCTV cameras, motion sensors, and access control systems into one central system. This type of system provides a higher level of security through automated detection and alerting, allowing building administrators to quickly identify potential threats or unauthorized access attempts.
With the rapid advancement of access control technology for buildings, it is important for businesses to stay up to date with these new trends in order to ensure their premises are secure.
In conclusion, access control technology for buildings has seen a surge in new trends and innovations over the past few years. From smartphone-enabled systems to automated access controls and integrated security systems, there are now many options available that can provide businesses with greater levels of protection and convenience. By staying up to date on these new technologies, companies can ensure their premises remain secure from unauthorized access attempts while also providing employees with more efficient ways to gain entry into their building.