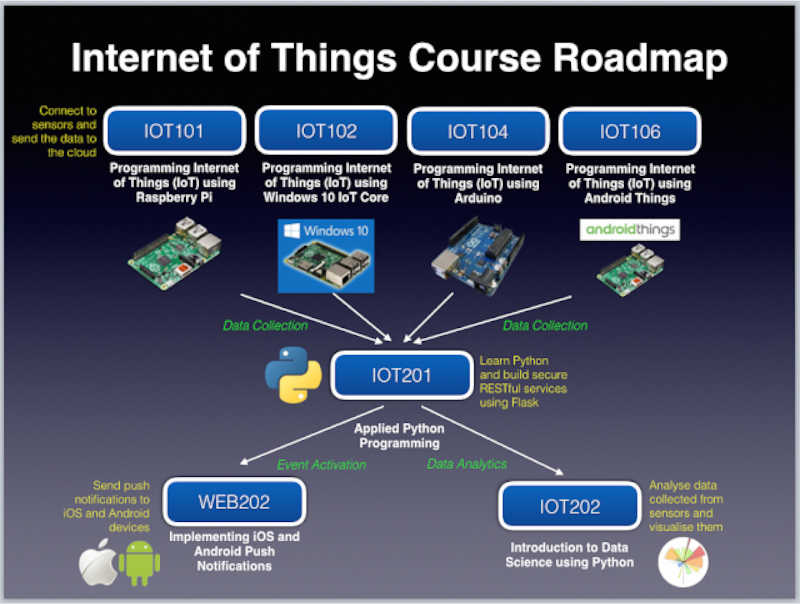
The Internet of Things (IoT) refers to the growing network of physical devices connected to the internet. That includes everything from cars and home appliances to factory machinery and medical equipment. By embedding sensors and other internet-connected technologies into everyday objects, we can collect data and use it to improve our lives in various ways.
As the numbers of connected devices continue to rise, there is an increasing demand for developers skilled in creating applications and systems that can effectively manage this vast network of data. If you are considering a career in IoT development, here are a few things to keep in mind.
IoT Career Opportunities
There are many different career paths available.
Internet of Things Developer
As the demand for IoT devices and solutions grows, so does the need for developers who can create them. IoT developers are responsible for designing and implementing software solutions that enable devices to connect to the internet and exchange data. They must have an excellent understanding of networking protocols and be able to work with various hardware platforms. Developers with experience with embedded systems, networking, and security are well-positioned to take advantage of this growing trend.
Internet of Things Engineering
IoT testing engineers ensure that IoT products function properly and meet customer expectations. They must be able to design test plans that simulate real-world conditions and identify potential issues with products before they are launched.
IoT Architect
An IoT architect is responsible for designing and overseeing the implementation of an organization’s IoT strategy. They require a deep understanding of technology trends and the ability to translate business needs into technical requirements.
IoT Data Scientist
Data is an integral part of successful IoT implementation. Data scientists who can collect, analyze, and interpret data from IoT devices will be in high demand as organizations look to make sense of all the data they’re collecting.
IoT Project Manager
A successful IoT project requires careful planning and coordination among multiple teams. Project managers with experience delivering complex technical projects will be well-suited to manage these initiatives.
Business Analyst
As IoT solution becomes more commonplace, organizations need help understanding how to best use these new technologies to achieve their business goals. Business analysts familiar with business and technology concepts will be uniquely positioned to advise businesses on how to exploit the best opportunities presented by the IoT.
Regarding careers on the Internet of Things, the sky is the limit. With so many different industries starting to adopt IoT technology, many IoT related jobs are available for those with the right skill set. Yalantis is a leading company in IoT development. Their team has developed innovative IoT solutions for various clients, from connected medical devices to smart home systems. If you are on the hunt for an exciting career in IoT, then Yalantis is worth checking out.
Qualifications & Skills Requirements
A Strong Coding Foundation
While the specific programming languages you’ll need to know will vary depending on the platform you’re working on, being able to code well is essential for any developer. In addition, it’s also important to have experience with various development tools and frameworks. The specific ones you’ll need will again depend on the platform you’re targeting, but knowing how to use them is crucial for any developer.
Experience With Big Data and Cloud Computing
IoT devices generate a lot of data, and efficiently processing and storing that data is essential for any IoT system. Experience with big data platforms like Hadoop or Spark is a major plus, as is experienced with cloud services like AWS or Azure.
Experience With Hardware
Many IoT applications interact directly with physical devices, so understanding electronics and circuits can be very helpful. Alternatively, if you’re more interested in software, experience with embedded systems can also be helpful.
Ability To Work with Databases
No matter what platform you’re working on, chances are you’ll need to be able to work with databases. Knowing how to query and update data is essential for any developer, so being proficient in a popular database language like SQL is a must. Additionally, experience with NoSQL databases like MongoDB or Cassandra can be helpful.
Excellent Problem-Solving Skills and A Willingness to Learn New Technologies
IoT is a rapidly changing field, so it’s important to be able to learn new technologies quickly. Additionally, since IoT systems are often complex, being able to solve problems effectively is essential for any developer working in this field.
Best IoT Developer Courses to Start a Career
If you’re considering a career in IoT development, here are four courses to help you get started.
Introduction to the Internet of Things by Udacity
The Internet of Things is one of the hottest new areas in tech, and Udacity’s Introduction to the Internet of Things course is the perfect way to start learning about it. The course covers all the basics of IoT, from an introduction to sensors and actuators to working with data and connecting devices to the cloud. You’ll even get to build a simple connected device as part of the course. With over 4 hours of content, this is one of the most comprehensive introductory IoT courses available. And best of all, it’s completely free.
Building Connected Devices with Azure IoT by Microsoft
This course from Microsoft will teach you how to build connected devices using Azure IoT, Microsoft’s platform for the Internet of Things. You’ll learn how to connect devices to Azure IoT, collect and analyze data from them, and use Azure services to build complete IoT solutions. The course is aimed at developers with some experience in C# or JavaScript, and it requires a paid subscription to access all the material. However, a free trial is available, so you can check out the course before deciding whether it’s worth the investment.
Getting Started with the Internet of Things by edX
This introductory course from edX will give you a broad overview of the field of IoT, covering everything from connected devices and sensors to data analysis and security concerns. You’ll also get to work with popular IoT platforms like Arduino and Raspberry Pi as part of the course. The course is free to take, but there is a fee if you want a certificate of completion.
Programming for the Internet of Things by Coursera
This Coursera course teaches you how to program for the Internet of Things. You’ll learn about popular IoT platforms like Arduino and Raspberry Pi, and you’ll get a chance to build your own connected devices as part of the course. The course is aimed at developers with some experience in Java or Python, but it doesn’t require any prior knowledge of IoT. The course is free to take, but there is a fee if you want a certificate of completion.
Conclusion
IoT is a rapidly growing field with immense potential. If you have the right skills and qualifications, then a career in IoT development could be the perfect fit for you. And with the help of courses like those listed above, you can learn about IoT development today. Enroll in a course and start your journey towards a career in this exciting new field today.