Video files play an essential role in the modern world as your life, in a way, revolves around them. Your important data is stored in video form if you are a professional videographer or a content creator. In personal life, many memories are stored in this form, from birthdays to weddings and more. MP4 and MOV are the most widely used video formats for creating and storing videos. So, if your important MP4 or MOV files get corrupted, it can hurt you greatly.
Luckily, now files getting corrupted doesn’t mean that these are gone. With the Wondershare Repairit video repair tool, you can easily repair even severely damaged MP4 and MOV files. We will explain the difference between MP4 and MOV, the reasons behind data corruption, and how to repair MP4 and MOV files.
Contents
- 1 Part 1: Major Differences Between MP4 and MOV Video Formats
- 2 Part 2: Primary Causes Behind MP4 or MOV Files Corruption
- 3 Part 3: The Walkthrough of Repairing MP4 and MOV Files Using Wondershare Repairit
- 4 Step 1: Selecting your MP4 or MOV Files
- 5 Step 2: Repairing your Videos
- 6 Step 3: Securing your Repaired Files
Part 1: Major Differences Between MP4 and MOV Video Formats
MOV, developed by Apple, and MP4, developed by ISO, are among the most used video format in the digital world. MOV is the default and goto format for all Apple devices, while MP4 is supported by all operating systems, video players, and editors. MP4 and MOV work on the lossy compression algorithm, but MOV still retains high quality and boosts larger video.
Regarding size scalability, MP4 is ideal as it could be scaled to the desired size while maintaining quality, though not as high as MOV offers. Due to its ability to retain high quality and being easy to encode, MOV is widely popular when it comes to professional video creators. MP4 is mostly popular with content creators due to its availability on a wide range of devices and flexibility regarding file size.
Part 2: Primary Causes Behind MP4 or MOV Files Corruption
There are many reasons behind the corruption of your MP4 and MOV files. It can range from malicious virus attacks to failed file transfers or because of a sudden system shutdown. The files can also be corrupted if you try to run them with incompatible software. Below are a few of the main reasons mentioned in detail:
1. Virus or Malware Attack
A virus or malware attack can affect and corrupt data on your system, making it useless to you. Video files are usually very susceptible to virus attacks making them a prime target. You should always create a backup of your essential data or use good anti-virus software.
2. Improper System or Software Shutdown
MP4 or MOV files can also get corrupted if you run them and a sudden system shutdown occurs. It can easily make the file being played corrupted. Similarly, if the software you use to play or edit MP4 or MOV files gets closed suddenly, it can corrupt the file.
3. Disruption in File Transfer or Download
Video files can also get corrupted if you export them from an external device like a USB or external storage device, and the process gets disrupted in between. It can also happen if you copy files from one place to another. Similarly, in the case of downloading the file, slow internet speed or loss of connection can result in file corruption.
4. Improper Conversion and Compression
Your MP4 or MOV files can also become corrupted during conversion to another format if the process is disturbed. It can also be the case that the converter you were using was lackluster. In the same way, if you are not able to properly compress the files, your MP4 and MOV files can get corrupted.
5. Inappropriate Read and Write and Broken Headers
All the media files have an internal structure and set of written code that is constantly being modified when we run those files. So, files can get corrupted if you are running your MP4 or MOV files with an incompatible or corrupted media player. Missing or broken headers of MP4 and MOV files can corrupt them.
Wondershare Repairit is, without a doubt, the most fantastic tool currently available in the market for repairing MP4 and MOV files. We recommend Wondershare Repairit because of its user-friendly interface, ease of the repairing process, and support for 15+ video formats. Aside from MP4 and MOV, it supports other video formats like MKV, 3GP, AVI, FLV, etc. It also allows repairing files in batch and multiple formats simultaneously.
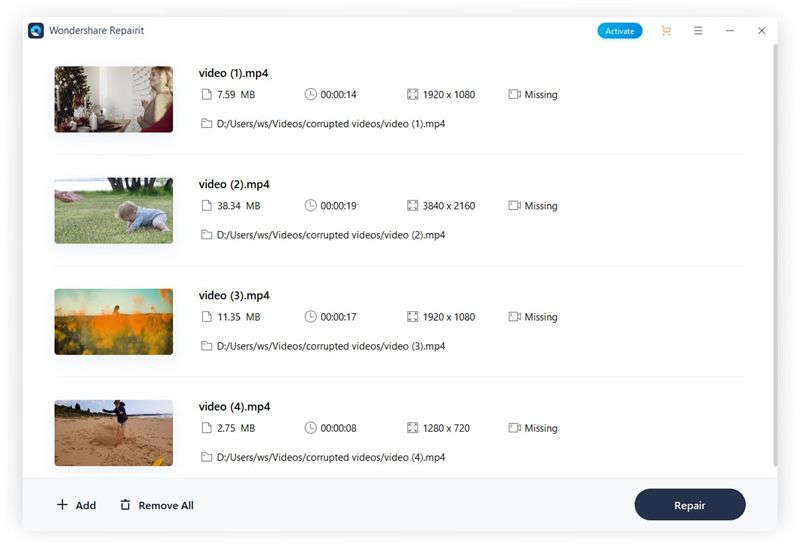
When you add your corrupted files, it shows you the information regarding File Name, File Path, File Size, Video Watching Time, Video Resolution, and Filming Equipment. If a general repair procedure doesn’t repair your files, you can choose Advanced Video Repair for your damaged videos.
The Advanced Video Repair function asks you to provide a sample file, preferably created in the same format by the same device, to repair your corrupt file. It will fix your file using the sample file as a basis. Below are the detailed steps explaining the repairing process:
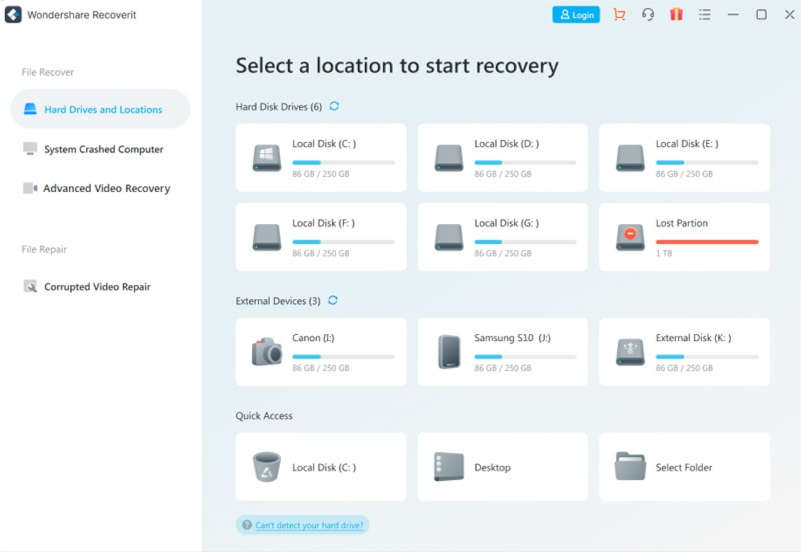
Step 1: Selecting your MP4 or MOV Files
Start the Repairit and select your corrupted files by clicking the “Add” button on the interface in the “Video Repair” tool. If you have multiple corrupted files, you can add them simultaneously, even if they are in a different format. After adding your MP4 and MOV files, you can see all the details regarding them on the interface.
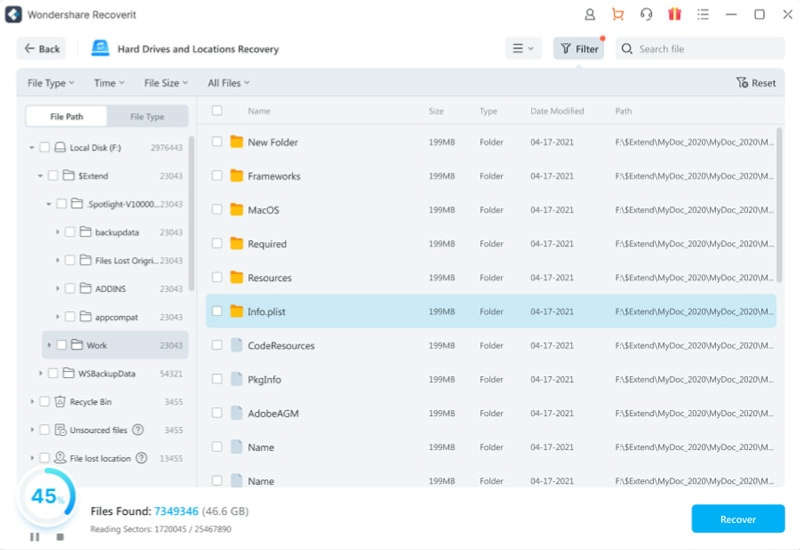
Step 2: Repairing your Videos
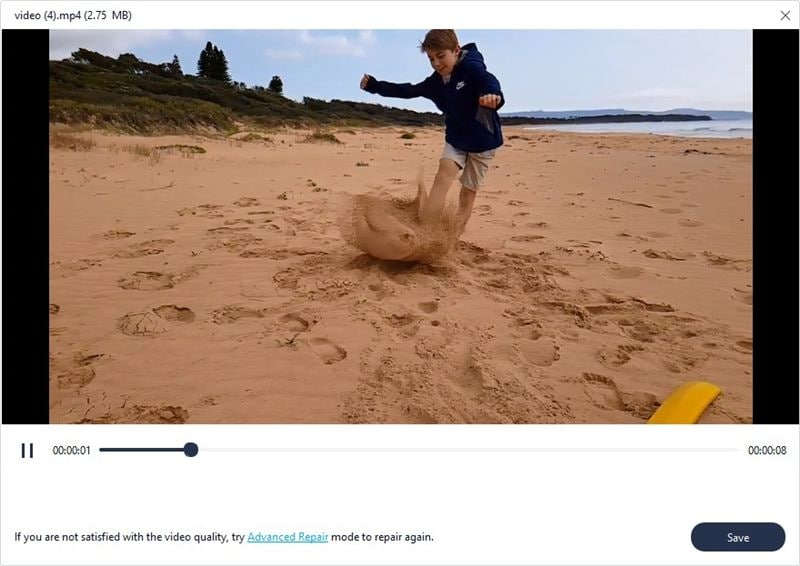
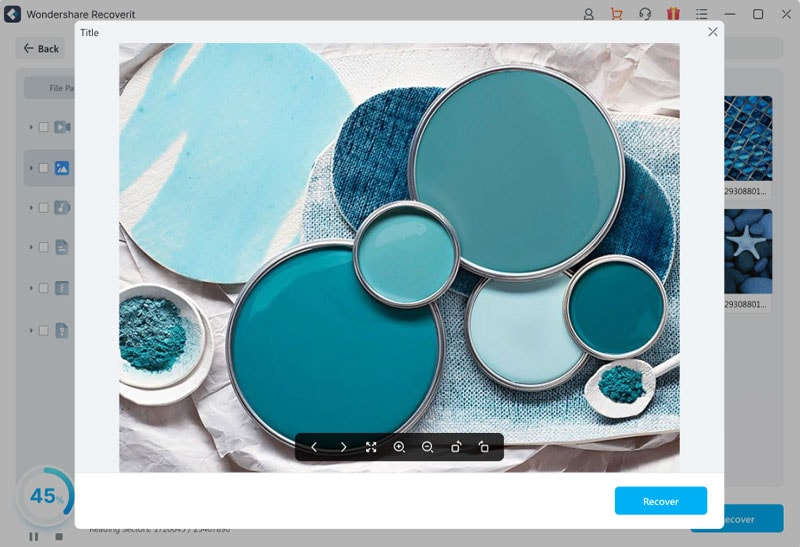
After making sure that the targeted files have been uploaded, click the “Repair” button, and it will start repairing the files. After the process, you can preview the files by clicking on the “Preview” button separately for each video file.
Step 3: Securing your Repaired Files
Now that you have previewed the files and are satisfied with the results, you can store the files into secure location. To do that, click the “Save” button and provide the desired location, ensuring it is different from where the original corrupted files were located. Wait for a few seconds, and files will be stored and ready to use.
Conclusion
There is usually always essential data stored in the form of videos in our daily life. Loss of that data can be problematic as it can create trouble and hinder your working life. Similarly, it can make you feel bitter after losing memorable videos of your life. If your essential MP4 or MOV file got corrupted, download the Wondershare Repairit now and use it to repair your important files. Along with videos, it also offers photos, audio, files, and an email repairing tool.