If you have lost or forgot the Windows administrator password then it could be a lot inconvenient than you can imagine especially if your computer contains all the important and confidential data that you cannot afford to lose anytime sooner. People often choose to format their computer in these situations but it will really damage all the encrypted files on your PC and there’s a high chance that you will lose them forever.
Certainly, you can try to look at your online vaults and email account to search for your password but if nothing seems to be working anymore then use the tricks and tweaks shared in this article to reset Windows administrator account password.
Part 1. Reset Windows 10 Administrator Account with Reset Disk
Creating a password reset disk or restore point is one of the top features provided by the Windows operating system. Perceptibly, you need to take these precautions before you forget your computer password to make this method work. So, if you are a wise and cautious guy then you must have made a password reset disk before you forgot your computer password.
Step 1: Insert the flash drive that you wished to create the password reset disk.
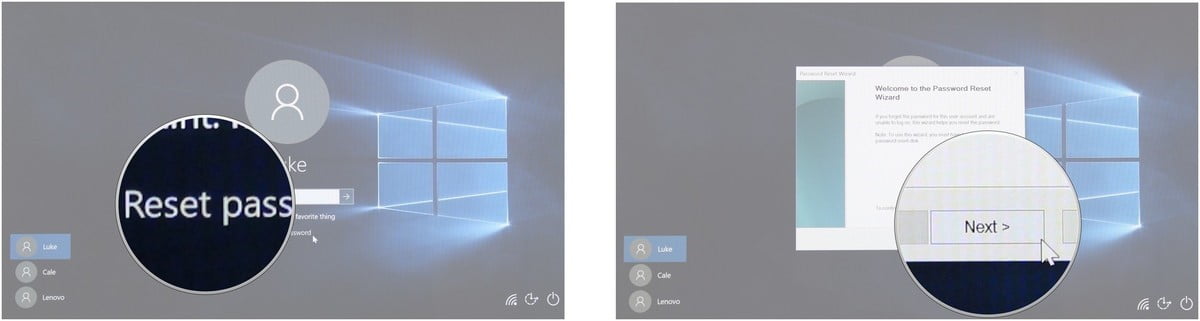
Step 2: Under the password field, click on “Reset Password” and a new password reset wizard window will pop up.
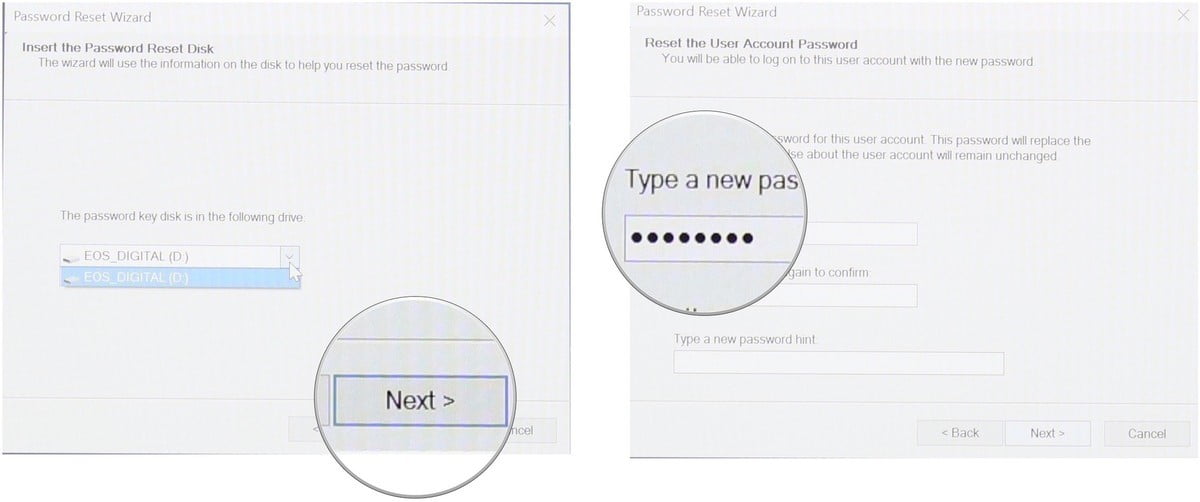
Step 3: Choose where you have saved the password-reset disk and follow through the process.
Step 4: Lastly, change your computer password and finish the process.
Use the new setup password to access your system without any problem.
Cons:
- Password reset disks must be made before forgetting your computer password.
- Works with an only particular computer from which the password-reset disk is created not any others.
Part 2. Reset Windows 10 Password With Command Prompt
Command Prompt is one of the most underestimated app but in reality, it can perform some critical tasks that cannot be performed by any other tools. One of them is cracking your own Windows administrator account password. Follow these steps to reset Windows 11 password with command prompt –
Step 1: Insert the Windows bootable disc on your PC and restart it.
Step 2: Select the “Repair Your Computer” option and continue with the process.
Step 3: Click on “Troubleshoot” then Advanced followed by Command Prompt.
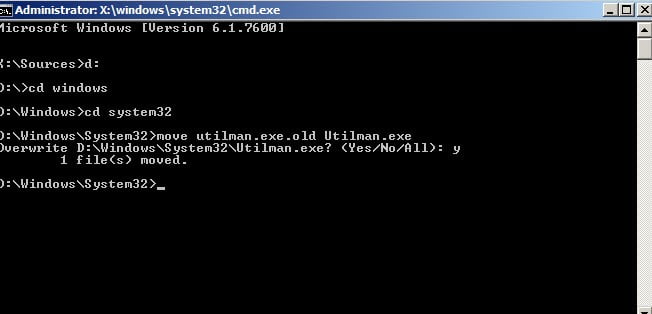
Step 4: Type in the following lines when the command prompt app opens –
MOVE C:\Windows\System32\Utilman.exe
C:\Windows\System32\Utilman.exe.bak
Press enter to execute and reboot your PC again.
Step 5: On the boot screen, press the Shift key 5 times to launch the command prompt app.
Step 6: Write the follow line inside the command prompt app –
“net user administrator mynewpass”
Obviously, you will have to replace “mynewpass” with your chosen password.
Reboot and use this password to enter into your PC.
Cons:
- Programming knowledge is required.
- Complex and difficult method to apply.
Part 3. Reset Windows Password With iToolab UnlockGo
iToolab UnlockGo will assist you to produce a password reset disk with the help of a CD or USB drive. You may then use the password reset disk to unlock your protected PC. It works with all Windows versions and with almost any kind of password like PIN, Text and Picture as well as even help you to change Microsoft account password too.
Requirements:
- A blank CD or Pen Drive.
- A working Windows computer.
- iToolab UnlockGo (Learn more)
Working Steps:
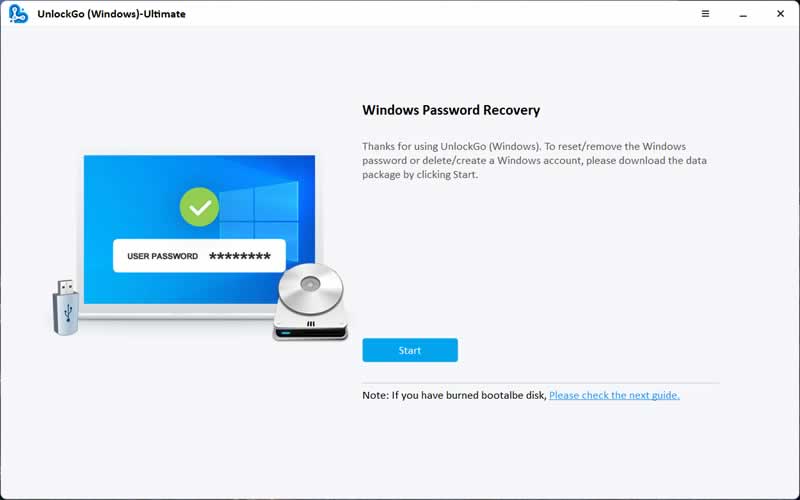
Step 1: Install iToolab UnlockGo Windows password reset tool on the working Windows computer and launch to see the main screen of the tool. Now click “Start” and wait to finish downloading the required data package.
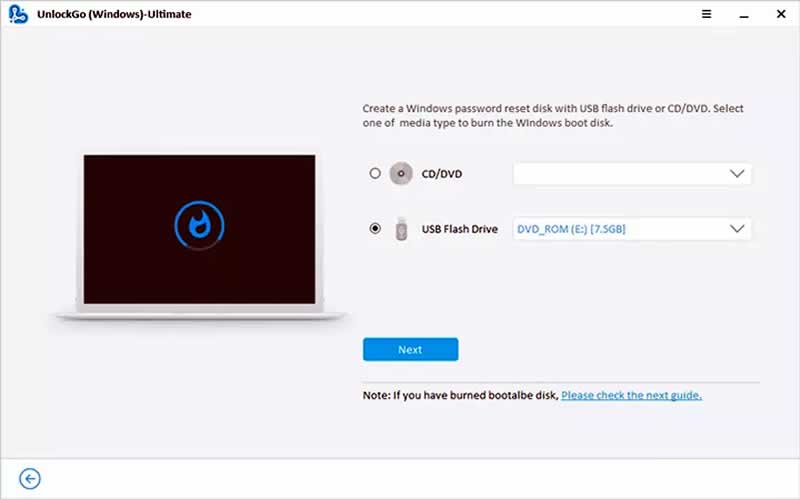
Step 2: Insert the pen drive or CD and select the appropriate option and click “Next”.
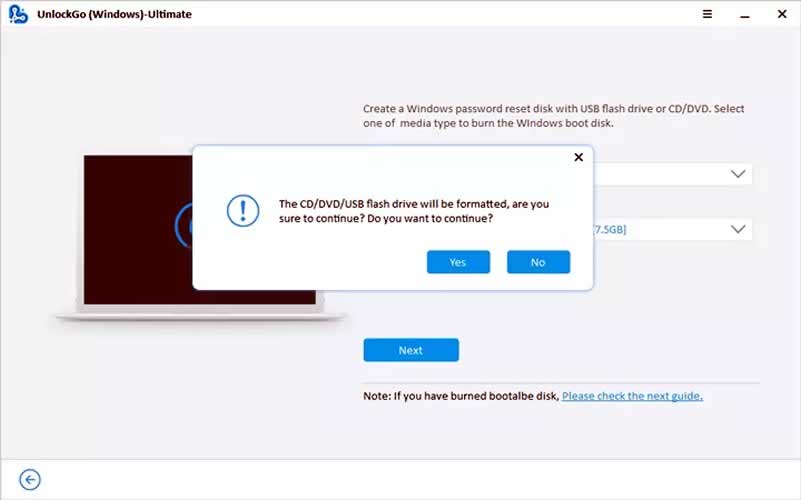
Step 3: Now, a window will pop up asking for your confirmation to burn the Windows boot disk. Tap “Yes” to allow UnlockGo to start burning a password reset disk. Once it is done, you can eject the flash drive.
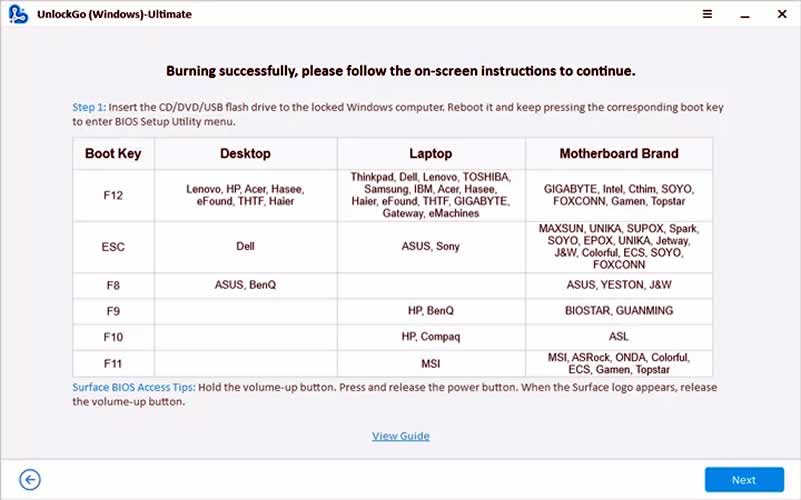
Also, check out and follow the on-screen instructions displayed after burning to unlock your locked computer.
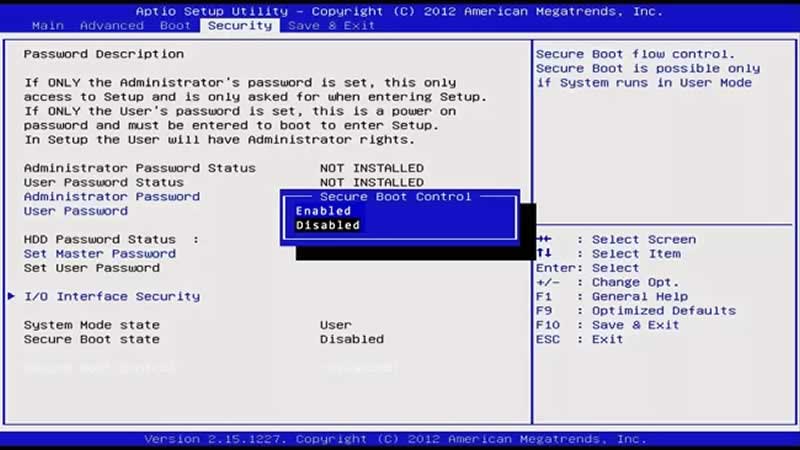
Step 4: Plug in the flash drive on the locked computer and turn it on. Make sure the “Secure Boot” option is “Disabled” in BIOS before this process.
Step 5: The program will be opened upon startup. Choose your Windows version and click “Next”.
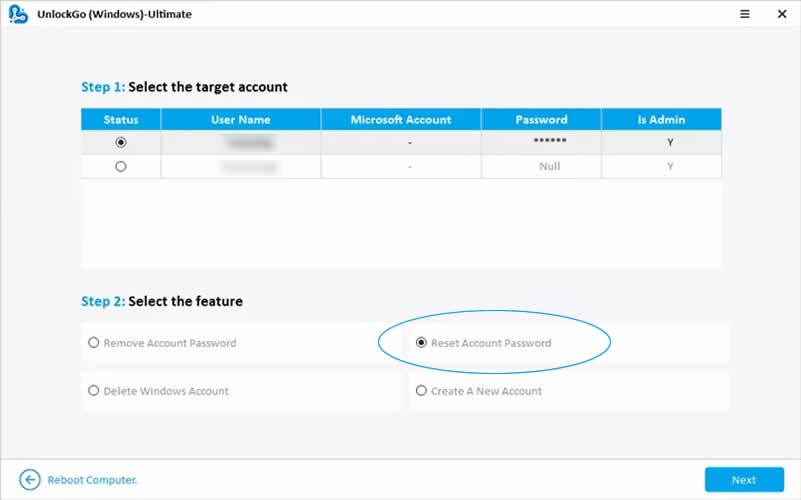
Step 6: Select the administrator username from the list. Then click on “Reset Account Password”.
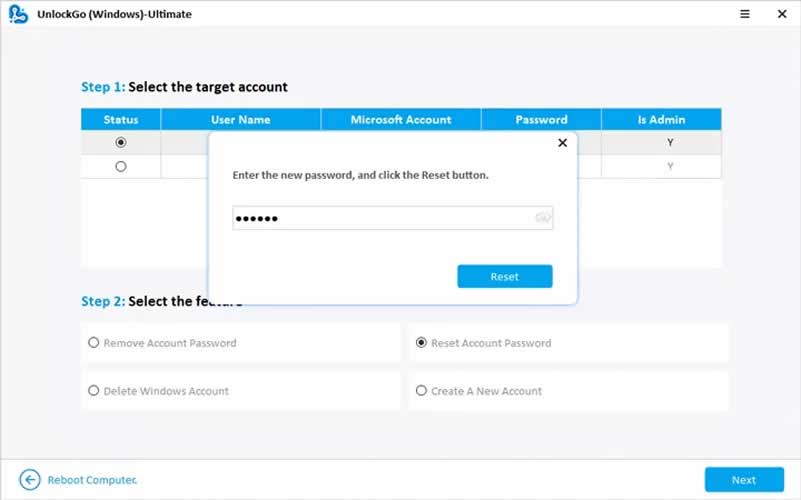
Step 7: Now, a pop up will ask you to type the new password and click the “Reset” button. That’s it; your Windows password has been reset successfully. Click “Restart” to enter the new password to access your computer.
To be noted, with the help of iToolab UnlockGo, you can also remove the Windows password by choosing the option “Remove Account Password” in Step 6 or delete or create a Windows account by either choosing “Delete Windows Account” or “Create A New Account”.
Conclusion:
In the future, try to make a password reset disk for all of your Windows computers so that you can unlock it if you forget the password. However, if you fail to do that, then don’t forget iToolab UnlockGo Windows password recovery tool is always there to serve you and rescue you from your embarrassing situations. This is a life-saving tool considering it doesn’t erase any data from your computer.